Cisco 4402 Configuration Guide - Page 42
Click on Next and then Edit Profile. - replacement
 |
UPC - 882658039997
View all Cisco 4402 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 42 highlights
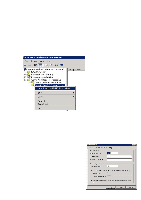
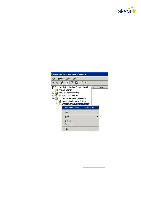
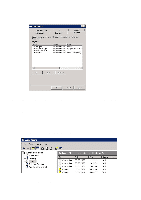
student.school.no is the connection to eduroam and forwards authentication to the employee.school.no RADIUS server. The "Employee" RADIUS server is the last in the series and receives authentications it is to use and forwards them. Criteria for "Connection Policies" on the student.school.no RADIUS server: .*@student.school.no - All students, authenticated locally .*@employee.school.no - All employees, sent to the "Employee" RADIUS server .*@.* - All other users, sent to the "Employee" RADIUS server Criteria for Connection Policies on the "Employee" RADIUS server: .*@employee.school.no - All employees, authenticated locally .*@.* - All other users, sent to the eduroam server Select "User-Name" and click on "Add". Fill in the criteria: for example ".*@student.school.no" specifies that all users who type in [email protected] shall be authenticated using this policy. Click on "Next" and then "Edit Profile". On the "Authentication" tab, specify where the authentication request shall be directed: • If one selects "Authenticate request on this server" the user is authenticated on this RADIUS server and the domain of which the user is a member. In that case: • Click on the "Attributes" tab • Select "Attribute: User-Name" and click on "Add" • Under "Find", type:(.*)@(.*) and under "Replace with", type: $1 • One may also select "Forward requests to the following remote RADIUS server group for authentication": the authentication request is then forwarded to one of the server groups created in Step 4. Click on "OK" followed by "Next" and "Apply". 42