Cisco WET200 User Guide - Page 20
Switch > MAC Based ACL - wireless g business
 |
UPC - 745883578320
View all Cisco WET200 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 20 highlights
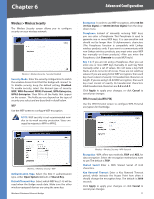
Chapter 6 Advanced Configuration Port-Based In port-based VLAN mode, the wireless bridge uses a portbased VLAN map to limit the traffic between the ports. A VLAN can include any of the five physical Ethernet ports (ports 1-5) as well as port 6, which controls the wireless interface and CPU access (management traffic and webbased utility access). NOTE: The default port-based VLAN settings consist of connections between port 6 and each of the five Ethernet ports. This is to allow access to the web-based utility from any of the Ethernet ports. In addition, the connection between ports 1 and 6 is permanent and cannot be changed. This ensures that you can always access the web-based utility through at least port 1, regardless of your particular port-based VLAN settings. Switch > VLAN - Port-Based Output Vector Use these fields to configure your VLANs as follows: 1. Each row of the table corresponds to one of the ports. For each port, specify its connections by selecting all of its exit ports. For example, to specify a VLAN connection from port 1 to port 2, select 2 in the row labeled Port 1. 2. Each exit port you select specifies a unidirectional connection only. (In the example in step 1, the direction is from port 1 to port 2.) To automatically add the connection in the opposite direction (from port 2 to port 1 in the example), click Configure Bi-directional. 3. When you are finished defining the connections for the VLAN(s), click Apply Port VLAN Settings to save and activate your VLAN configuration. Wireless-G Business Ethernet Bridge Switch > MAC Based ACL Switch > MAC Based ACL An Access List (ACL) is a list of source MAC addresses that is used to grant or deny access. If a packet passes from the wireless port to a LAN port or vice versa, the Bridge will check if the packet's source MAC address matches any entry in the access list, then use the match result to pass or drop the packet. However, packets from LAN port to LAN port are not checked. You can select from two types of Access Lists. A Block list blocks specific MAC addresses specified in the table; all other MAC addresses are accepted. An Accept list only accepts the MAC addresses listed in the table; all other MAC addresses are blocked. Access List Type To disable the Access List feature, keep the default setting, Disabled. To enable Access Lists, select Accept or Block, then click Apply Global Setting. If you choose to use an Accept list, you must remember to include your computer's MAC address in the list before you click Apply. Failure to do so may result in your computer being denied access to the device. New Block Entry To block packets with a specific MAC address, enter the MAC address in this field, and click Add Block Entry. To unblock the MAC address, enter the MAC address in the field, click Delete Block Entry, then click Apply Global Setting. Block List Displays a list of blocked MAC addresses and number of packets dropped for each address. New Accept Entry To accept packets with a specific MAC address, enter the MAC address in this field, and click Add Access Entry. To unaccept the MAC address, enter the MAC address in the field, click Delete Access Entry, then click Apply Global Setting. Accept List Displays a list of accepted MAC addresses and number of packets accepted for each address. Drop Count, Accept Count When Access List is enabled, these display the total number of packets dropped and accepted. Click Refresh to display the latest information. 16