Dell PowerConnect W-Series FIPS Dell PowerConnect W-AP92/93, W-AP105, W-AP175 - Page 40
Critical Security Parameters
 |
View all Dell PowerConnect W-Series FIPS manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 40 highlights
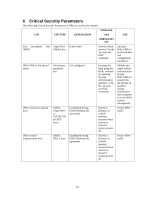
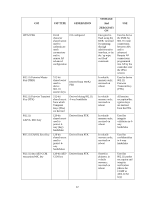
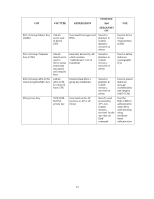
6 Critical Security Parameters The following Critical Security Parameters (CSPs) are used by the module: STORAGE CSP CSP TYPE GENERATION And USE ZEROIZATI ON Key Encryption Key Triple-DES Hard-coded (KEK) 168-bits key Stored in flash, zeroized by the 'ap wipe out flash' command. Encrypts IKEv1/IKEv2 preshared keys and configuration parameters IKEv1/IKEv2 Pre-shared secret 64 character preshared key CO configured Encrypted in flash using the KEK; zeroized by updating through administrative interface, or by the 'ap wipe out flash' command. Module and crypto officer authentication during IKEv1/IKEv2; entered into the module in plaintext during initialization and encrypted over the IPSec session subsequently. IPSec session encryption keys 168-bit Triple-DES, or 128/192/256 bit AES keys; Established during Diffie-Hellman key agreement Stored in plaintext in volatile memory; zeroized when session is closed or system powers off Secure IPSec traffic IPSec session authentication keys HMAC SHA-1 keys Established during Diffie-Hellman key agreement Stored in plaintext in volatile memory; zeroized when session is closed or system powers off Secure IPSec traffic 40