Dell Powerconnect W-ClearPass Virtual Appliances W-ClearPass Policy Manager 6. - Page 26
Table 11, MAC Authentication Service Navigation and Settings
 |
View all Dell Powerconnect W-ClearPass Virtual Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 26 highlights
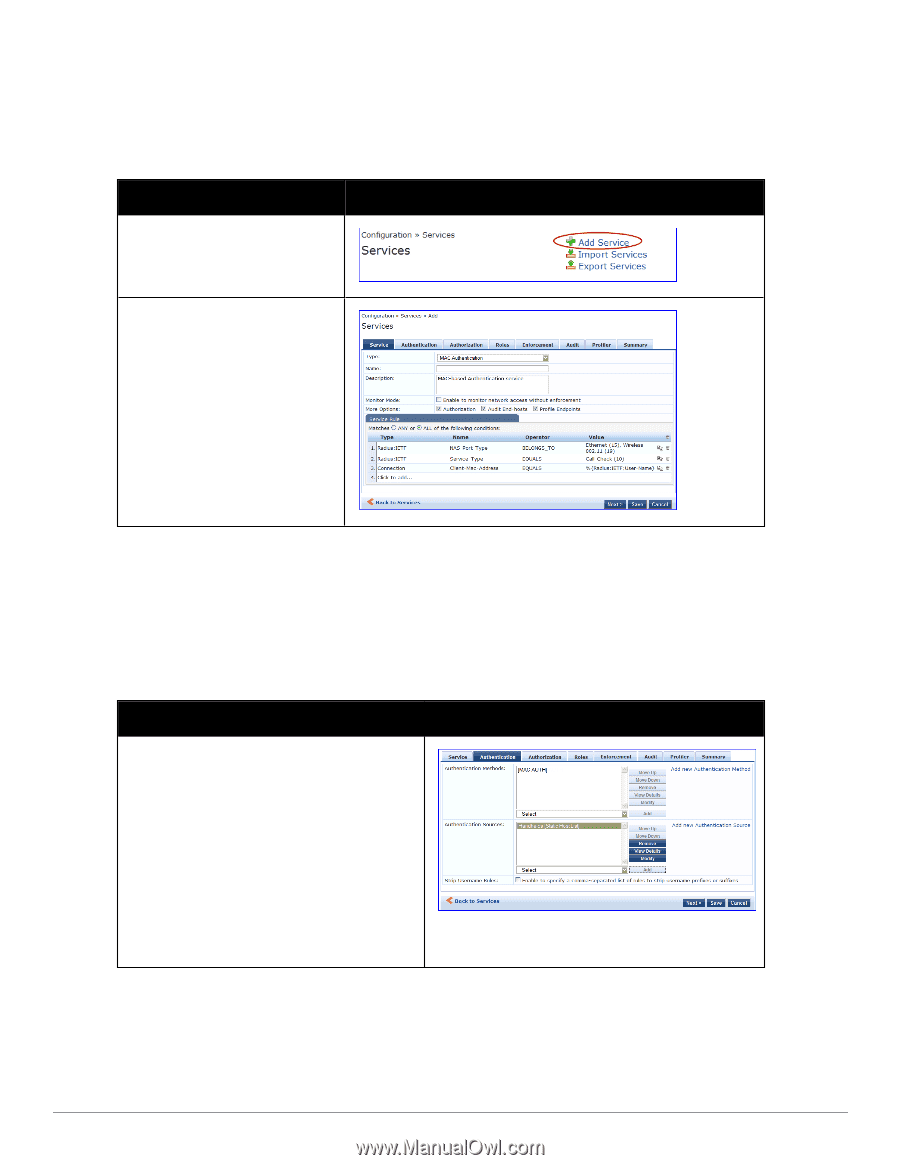
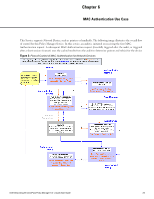
Configuring the Service Follow these steps to configure Policy Manager for MAC-based Network Device access. 1. Create a MAC Authentication Service. Table 11: MAC Authentication Service Navigation and Settings Navigation Settings Create a new Service: l Services > l Add Service (link) > Name the Service and select a preconfigured Service Type: l Service (tab) > l Type (selector): MAC Authentication > l Name/Description (freeform) > l Upon completion, click Next to configure Authentication 2. Set up Authentication Note that you can select any type of authentication/authorization source for a MAC Authentication service. Only a Static Host list of type MAC Address List or MAC Address Regular Expression shows up in the list of authentication sources (of type Static Host List). Refer to Adding and Modifying Static Host Lists "Adding and Modifying Static Host Lists" in the Dell Networking W-ClearPass Policy Manager User Guide for more information. You can also select any other supported type of authentication source. Table 12: Authentication Method Navigation and Settings Navigation Settings Select an Authentication Method and two authentication sources - one of type Static Host List and the other of type Generic LDAP server (that you have already configured in Policy Manager): l Authentication (tab) > l Methods (This method is automatically selected for this type of service): [MAC AUTH] > l Add > l Sources (Select drop-down list): Handhelds [Static Host List] and Policy Manager Clients White List [Generic LDAP] > l Add > l Upon completion, Next (to Audit) 3. Configure an Audit Server. This step is optional if no Role Mapping Policy is provided, or if you want to establish health or roles using an audit. An audit server determines health by performing a detailed system and health vulnerability analysis 26 Dell Networking W-ClearPass Policy Manager 6.0 | Quick Start Guide