HP Brocade BladeSystem 4/12 HP StorageWorks Fabric OS 6.x administrator guide - Page 131
Preparing the switch for FIPS, Overview of steps, Block Telnet, HTTP, and RPC using
 |
View all HP Brocade BladeSystem 4/12 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 131 highlights
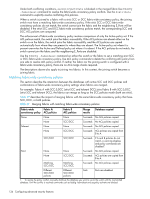
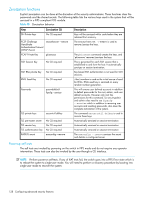
Table 41 FIPS mode restrictions Features FIPS mode Non-FIPS mode DH-CHAP/FCAP hashing algorithms Signed firmware Configupload/ download/ supportsave/ firmwaredownload IPsec Radius auth protocols SHA-1 MD5 and SHA-1 Mandatory firmware signature validation SCP only Optional firmware signature validation FTP and SCP Usage of AES-XCBC, MD5 and DH group 1 No restrictions are blocked PEAP-MSCHAPv2 CHAP, PAP, PEAP-MSCHAPv2 Preparing the switch for FIPS The following functionalities are blocked in FIPS mode. Therefore, it is important to prepare the switch by disabling these functionalities prior to enabling FIPS. • The root account is blocked in FIPS mode. Therefore, all root only functionalities will not be available. • HTTP, Telnet, RPC, SNMP protocols need to be disabled. Once these are blocked, you cannot use these protocols to read or write data from and to the switch • Configdownload and firmwaredownload using an FTP server will be blocked. See Table 41 on page 130 for a complete list of restrictions between FIPS and non-FIPS mode. IMPORTANT: Only roles with SecurityAdmin and Admin can enable FIPS mode. Overview of steps 1. Optional: Configure RADIUS server 2. Optional: Configure authentication protocols 3. Block Telnet, HTTP, and RPC 4. Disable BootProm access 5. Configure the switch for signed firmware 6. Disable root access 7. Enable FIPS To enable FIPS mode: 1. Log in to the switch using an account assigned the admin or securityAdmin role. 2. Optional: If the switch is set for RADIUS, modify each server to use only peap-mschapv2 as the authentication protocol using the aaaconfig --change or aaaconfig --remove command. 3. Optional: Set the authentication protocols a. Type the following command to set the hash type for MD5 which is used in authentication protocols DHCHAP and FCAP: authutil --set -h sha1 b. Set the DH group to 1 or 2 or 3 or 4 using authutil --set -g , where the DH group is represented by . 4. Block Telnet, HTTP, and RPC using the ipfilter policy command. You will need to create an IPFilter policy for each protocol. a. Create an IP Filter rule for each protocol, see "To create an IP Filter policy:" on page 116. Fabric OS 6.x administrator guide 131