HP G62-357CA Notebook Essentials - Windows 7 - Page 10
Protecting your privacy, Protecting the computer from power surges, Notebook Essentials
 |
View all HP G62-357CA manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 10 highlights
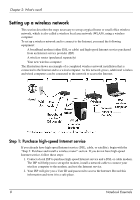
Chapter 2: What's next? Protecting your privacy When you use the computer for e-mail, network, or Internet access, it is possible for unauthorized persons to obtain information about you or the computer. To optimize the computers privacy protection features, follow these guidelines: ■ Keep the operating system and software updated. Many software updates contain security enhancements. ■ Use a firewall. Firewall software monitors incoming traffic on the computer to block messages that do not meet specific security criteria. Some firewalls also monitor outgoing traffic. Protecting the computer from power surges To protect the computer from the power surges that may be caused by an uncertain power supply or an electrical storm, observe these practices: ■ Plug the computer power cord into an optional, high-quality surge protector. Surge protectors are available from most computer or electronics retailers. ■ During an electrical storm, either run the computer on battery power or shut down the computer and unplug the power cord. ■ If applicable to your location, provide surge protection on the modem cable that connects the modem to a telephone line. Telephone line surge protectors are commonly available from computer or electronics retailers in many regions. 4 Notebook Essentials