Linksys WRT110-RM User Guide - Page 24
Applications and Gaming > DMZ, Port Range Triggering
 |
UPC - 745883585793
View all Linksys WRT110-RM manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 24 highlights
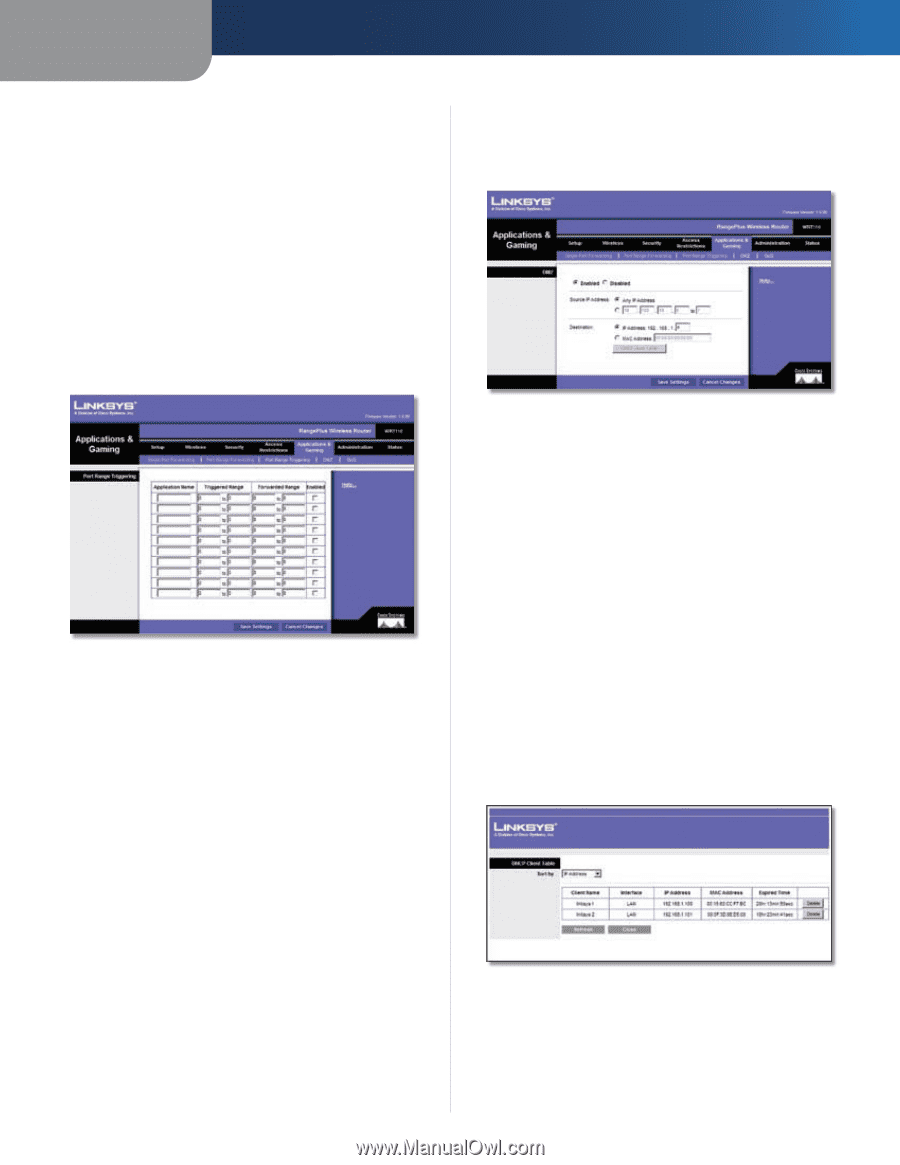
Chapter 3 Enabled Select Enabled to enable port forwarding for the applications you have defined. Click Save Settings to apply your changes, or click Cancel Changes to cancel your changes. Applications & Gaming > Port Range Triggering The Port Range Triggering screen allows the Router to watch outgoing data for specific port numbers. The IP address of the computer that sends the matching data is remembered by the Router, so that when the requested data returns through the Router, the data is pulled back to the proper computer by way of IP address and port mapping rules. Applications and Gaming > Port Range Triggering Port Range Triggering Application Name Enter the application name of the trigger. Triggered Range For each application, enter the starting and ending port numbers of the triggered port number range. Check with the Internet application documentation for the port number(s) needed. Forwarded Range For each application, enter the starting and ending port numbers of the forwarded port number range. Check with the Internet application documentation for the port number(s) needed. Enabled Select Enabled to enable port triggering for the applications you have defined. Click Save Settings to apply your changes, or click Cancel Changes to cancel your changes. Applications and Gaming > DMZ The DMZ feature allows one network computer to be exposed to the Internet for use of a special-purpose service such as Internet gaming or videoconferencing. DMZ hosting forwards all the ports at the same time to RangePlus Wireless Router Advanced Configuration one PC. The Port Range Forwarding feature is more secure because it only opens the ports you want to have opened, while DMZ hosting opens all the ports of one computer, exposing the computer to the Internet. Applications and Gaming > DMZ DMZ Any PC whose port is being forwarded must have its DHCP client function disabled and should have a new static IP address assigned to it because its IP address may change when using the DHCP function. Enabled/Disabled To disable DMZ hosting, select Disabled. To expose one PC, select Enabled. Then configure the following settings: Source IP Address If you want any IP address to be the source, select Any IP Address. If you want to specify an IP address or range of IP addresses as the designated source, select and complete the IP address range fields. Destination If you want to specify the DMZ host by IP address, select IP Address and enter the IP address in the field provided. If you want to specify the DMZ host by MAC address, select MAC Address and enter the MAC address in the field provided. To retrieve this information, click DHCP Client Table. DMZ > DHCP Client Table DHCP Client Table The DHCP Client Table lists computers and other devices that have been assigned IP addresses by the Router. The list can be sorted by Client Name, Interface, IP Address, MAC Address, and Expired Time (how 23