Ricoh Aficio MP C2050SPF Features Guide - Page 13
User Account Registration (User Account Enhance Unit), WPA Support (Wi-Fi Protect Access), Kerberos
 |
View all Ricoh Aficio MP C2050SPF manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 13 highlights
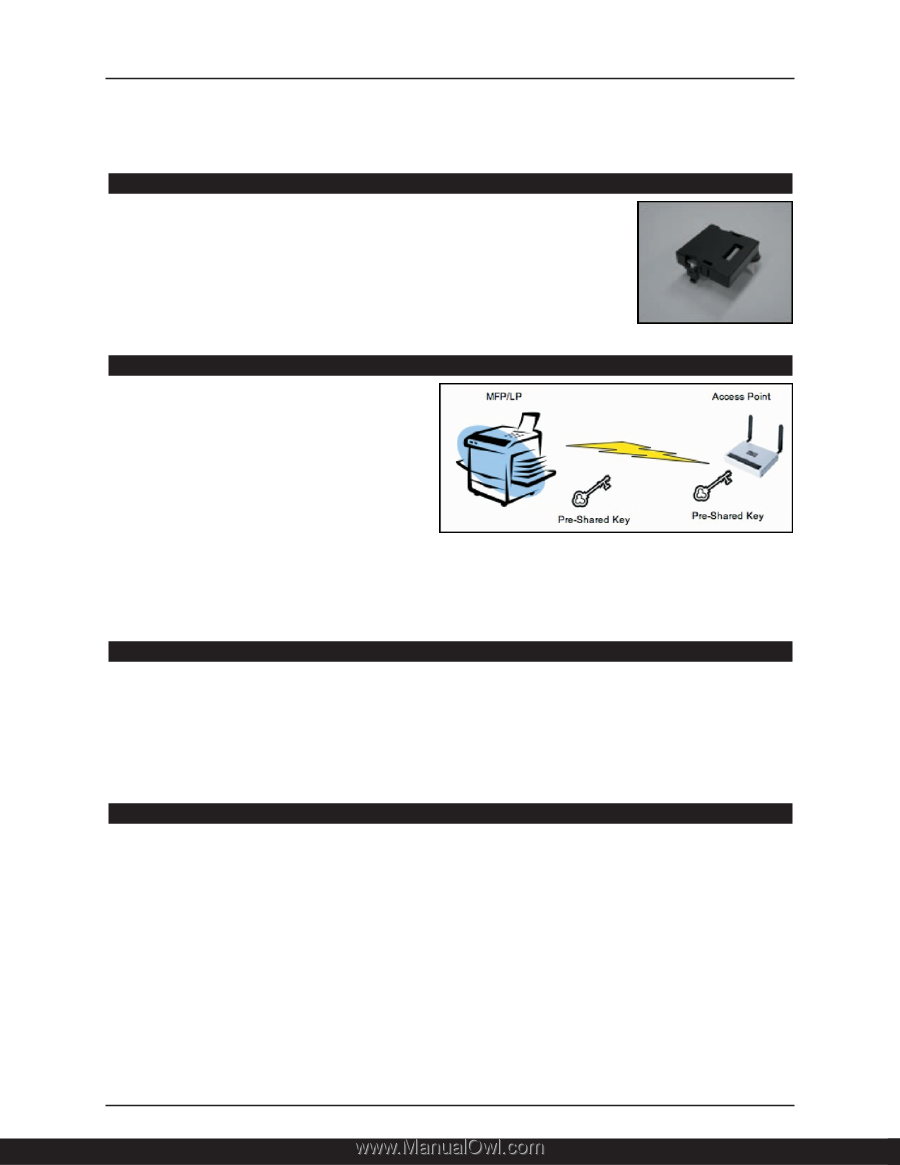
User Account Registration (User Account Enhance Unit) Most Ricoh devices allow customers to register up to 30 user accounts to track and limit user access. Installing the optional User Account Enhance Unit increases capacity to a maximum of 500 accounts to monitor device usage and restrict larger populations' accessibility to printing functions. Printer usage data is saved so that it can be exported to an Excel spreadsheet for reporting/usage analyses. WPA Support (Wi-Fi Protect Access) Used in conjunction with the IEEE 802.11a/b/g Wireless LAN option, WPA is a new security specification that addresses vulnerabilities in wireless communications. It provides a high level of assurance to enterprises, small businesses, and even home-based users that data will remain protected by allowing only authorized users to access their networks. "Personal" and "Enterprise" authentication and encryption features block intruders with wirelessly-enabled laptops from tapping into wireless networks in any environment, preventing the interception of data streams and passwords, or from using the wireless connection as an entry point into the customer data network. Kerberos Kerberos is a network authentication protocol designed to provide strong authentication for client/server applications by implementing secret-key cryptography. Many internet protocols do not provide any security for their passwords. Hackers employ programs called "sniffers" to extract passwords to gain access to networks. Sending an unencrypted password over a network is risky and can open the network to attack. Kerberos authentication helps to limit the risks caused by unencrypted passwords and keep networks more secure. 802.1X Wired Authentication 802.1X provides Network-port based authentication for point-to-point communication between network devices and a LAN port. By providing a point-to-point connection to a LAN port, communication will terminate if the authentication fails. 10