Ricoh Aficio MP C2800 Security Target - Page 55
O.audit, O.i&a, O.doc_acc, O.manage, O.mem.protect, O.net.protect, O.genuine, O.line_protect,
 |
View all Ricoh Aficio MP C2800 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 55 highlights
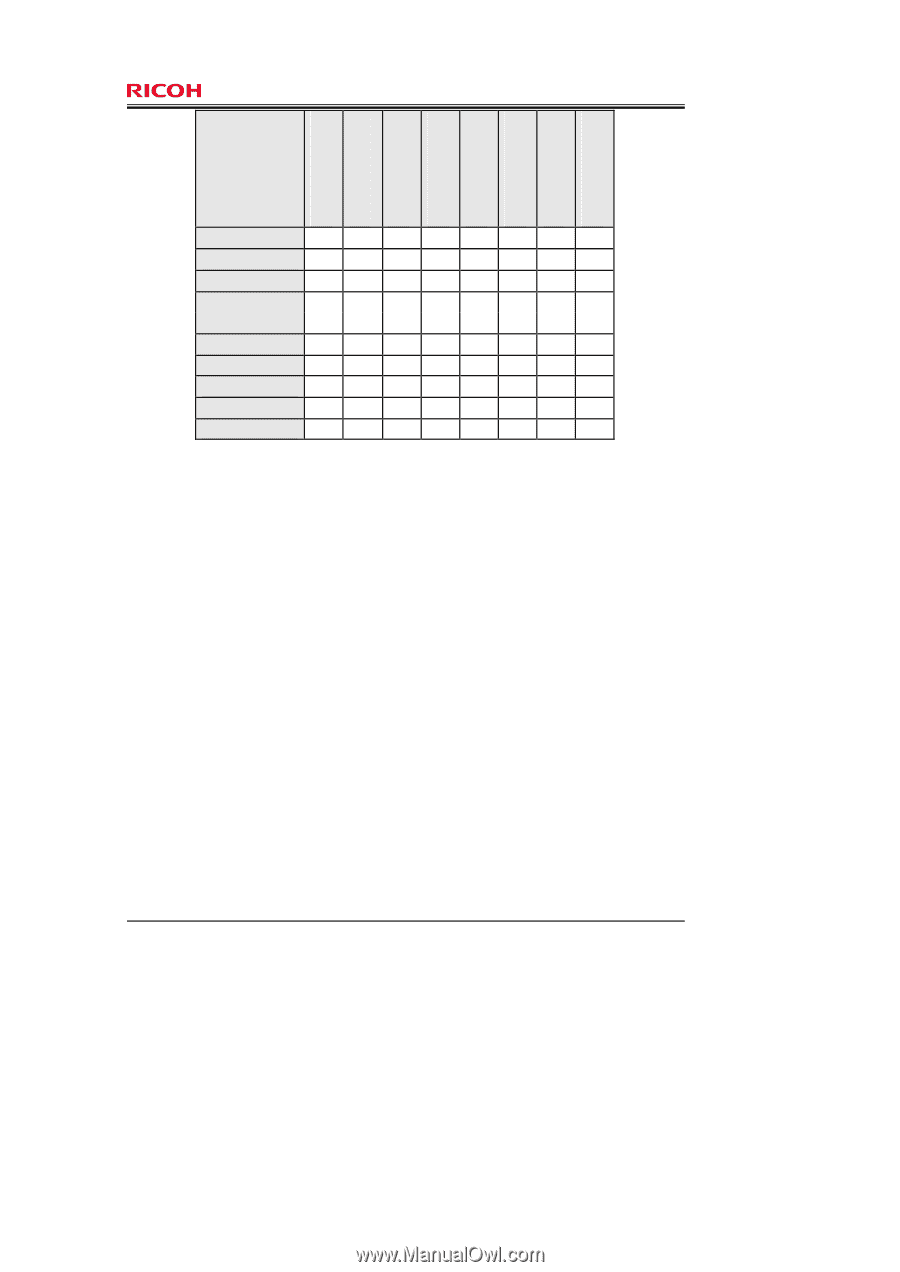
Page 55 of 80 O.AUDIT O.I&A O.DOC_ACC O.MANAGE O.MEM.PROTECT O.NET.PROTECT O.GENUINE O.LINE_PROTECT FIA_USB.1 FMT_MSA.1 FMT_MSA.3 FMT_MTD.1 FMT_SMF.1 FMT_SMR.1 FPT_STM.1 FPT_TST.1 FTP_ITC.1 FTP_TRP.1 v v v v v v v v v v v 6.3.2 Justification of Traceability This section describes how the TOE security objectives are fulfilled by the TOE security functional requirements corresponding to the TOE security objectives shown inTable 22. O.AUDIT Audit Following are the rationale behind the functional requirements corresponding to O.AUDIT in Table 22, and these requirements are included to fulfil the O.AUDIT specification. a ) Record audit logs To fulfil O.AUDIT, the performance of Security Functions should be recorded as audit logs. For this, FAU_GEN.1 generates audit information whenever an Audit Function starts and ends, whenever an identification or authentication function is performed, whenever users operate protected assets, whenever protected assets are encrypted, and whenever a major Management Function is performed. The log also records the date, time, type, subject identity, and outcome of each event. b) Provide Audit Function To fulfil O.AUDIT, access to audit logs should be restricted to the machine administrator only, and in a format that can be audited. For this, FAU_SAR.1 allows only the machine administrator to read audit logs, and FAU_SAR.2 prohibits persons other than the machine administrator reading audit logs. c ) Protect audit logs To fulfil O.AUDIT, audit logs should have adequate protection. For this, FAU_STG.4 protects audit logs from unauthorised deletion and prevents unauthorised tampering. If auditable events occur and the audit log files are full, FAU_STG.4 prevents loss of recent audit logs by writing the newer audit logs over audit logs that have the oldest time stamp. Copyright (c) 2009,2010 RICOH COMPANY, LTD. All Rights Reserved.