Seagate ST3300457FC Cheetah 15K.7 SAS Product Manual - Page 44
Power requirements, Supported commands
 |
View all Seagate ST3300457FC manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 44 highlights
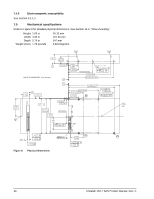
2. The download file must be signed and authenticated. 3. As with a non-SED drive, the download file must pass the acceptance criteria for the drive. For example it must be applicable to the correct drive model, and have compatible revision and customer status. 9.8 Power requirements The standard drive models and the SED drive models have identical hardware, however the security and encryption portion of the drive controller ASIC is enabled and functional in the SED models. This represents a small additional drain on the 5V supply of about 30mA and a commensurate increase of about 150mW in power consumption. There is no additional drain on the 12V supply. See the tables in Section 7.2 for power requirements on the standard (non-SED) drive models. 9.9 Supported commands The SED models support the following two commands in addition to the commands supported by the standard (non-SED) models as listed in Table 19: • Security Protocol Out (B5h) • Security Protocol In (A2h) 38 Cheetah 15K.7 SAS Product Manual, Rev. C