Dell PowerConnect W-IAP175P Dell Instant 6.2.0.0-3.2.0.0 User Guide - Page 48
requires Dell PowerConnect W-ClearPass, PowerConnect W-ClearPass Policy
 |
View all Dell PowerConnect W-IAP175P manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 48 highlights
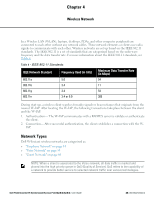
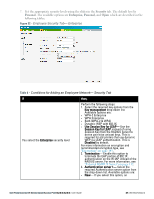
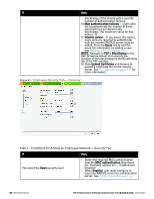
If You want to use the default security level, Personal then, external RADIUS server has to be configured to authenticate the users. For information on configuring an external RADIUS server, see "Authentication" on page 111. l InternalServer- If you select this option, users who are required to authenticate with the internal RADIUS server must be added. Click the Users link to add the users. For information on adding a user, see "Adding a User" on page 269. 4. Reauth interval- When set to a value greater than zero, the Access Points periodically reauthenticate all associated and authenticated clients. 5. Blacklisting- Select Enabled to enable blacklisting of the clients with a specific number of authentication failures. 6. Authentication survivability- This feature requires Dell PowerConnect W-ClearPass Policy Manager (6.0.2 and above) and is visible in the UI only when you select New to configure an external RADIUS server for authentication. If you select your RADIUS server as an internal server, then this feature is not applicable. When enabled, this feature allows W-Instant to authenticate the previously connected clients using EAP-PEAP authentication even when connectivity to Dell PowerConnect W-ClearPass Policy Manager is temporarily lost. Cache timeout (global)-Indicates the duration after which the authenticated credentials in the cache expire. When the cache expires, the clients are required to authenticate again. The supported range is 1 - 99 hours and the default value is 24 hours. 7. MAC authentication - Indicates per-user authentication using MAC address. Perform MAC authentication before 802.1X-Indicates per-user authentication using MAC address. This feature is optional. MAC authentication fail-thru-When this option is enabled, if MAC authentication fails, 802.1X authentication will be attempted. When this option is disabled, if MAC authentication fails, no further authentication will be attempted. 8. Click Upload Certificate and browse to upload a certificate file for the internal server. See "Certificates" on page 138 for more information. Perform the following steps: 1. Select the required key options from the 48 | Wireless Network Dell PowerConnect W-Series Instant Access Point 6.2.0.0-3.2.0.0 | User Guide