HP CM8000 Practical IPsec Deployment for Printing and Imaging Devices - Page 136
IKE Authentication: Kerberos
 |
View all HP CM8000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 136 highlights
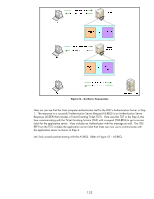
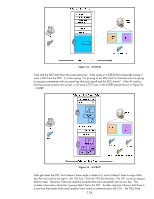
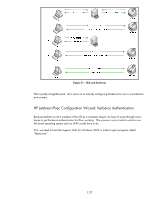
Figure 56 - TGS-REP Here we see the application server ticket is just an "opaque blob" to Vista as well. However, using the TGS/Vista session key, information about the application server ticket is also included so that Vista can communicate with the application server. Kerberos tries to use session keys and minimize the use of long-term keys (keys based upon the user's password) as much as possible. Kerberos also enforces a "need to know only" policy by using different keys to make parts of the packet that are intended for another endpoint "opaque blobs". The fact that the KDC has a copy of everyone's long term key and can generate session keys on the fly is what makes this type of exchange possible. IKE Authentication: Kerberos Kerberos authentication happens in IKE Phase 1. Let's look at a typical Kerberos exchange during IKE negotiation. Refer to Figure 57 - IKE and Kerberos. 136