HP ProBook 4525s HP ProtectTools Security Software 2010 - Page 11
Drive Encryption for HP ProtectTools - price
 |
View all HP ProBook 4525s manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 11 highlights
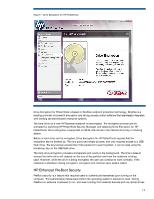
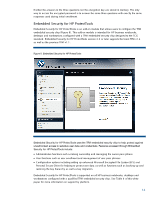
C onfiguration, Device Access Manager presents a device tree view derived from the W indows Device Manager. Individual devices or a n entire class of devices from the device tree can be selected. Access to the selected device can then be restricted by applying the policy to selected users or class of users. This level of configurability enables new client usage models, such as described in the scenarios below: • Scenario 1 : In a call center environment, call takers have full access to sensitive product and pricing information. The company however wants to protect this data and ensure that it is not removed from the premises. This can be accomplished by creating a Device Access Manager policy that prevents remova ble storage devices such as USB keys and writeable optical drives from being used by unauthorized users. • Scenario 2 : A company is making sensitive financial information available to an auditor and wants to protect this information from being copied or removed from the notebook. Device Access Manager can allow a policy where this user is denied access to any removable storage devices. Device Access M anager for HP ProtectTools is a single user client version. However, an enterprise version of Device Access M anager (HP ProtectTools Device Manager) is also available and allows the same policies to be configured and deployed remotely. For information on HP ProtectTools Device M a na ger, plea se refer to www.hp.com/ hps/ security/ products/ Drive Encryption for HP ProtectTools Drive Encryption is a full volume encryption (FVE) solution that encodes all information on the hard drive volume so it becomes unreadable to an unauthorized person. FVE is currently the preferred way to protect data on a hard drive. W ith Drive Encryption, you can encrypt or decrypt individual drives, create backup keys, and perform a recovery (Figure 7 ). 11