HP Visualize J5000 hp visualize workstation - Interoperable Security for HP-UX - Page 2
Introduction, Security Concerns
 |
View all HP Visualize J5000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 2 highlights
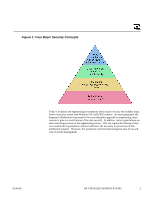
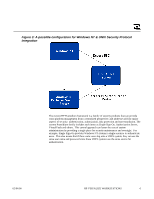
Introduction In order to provide integration and interoperability of engineering functions and information between HP-UX and Windows NT platforms, protection of resources and data must be assured. This secure engineering environment is most prevalent when an organization utilizes out-sourcing for engineering services of sub-components and processes. At first glance, it appears that there is little interoperability between HP-UX Security and that of Windows NT, as both operating systems provide unique capabilities for authentication, authorization and data protection that are inherently "uninteroperable". This can significantly increase the cost of system management in a heterogeneous network. The use and management of two different security processes also increases the possibility of compromising critical information. Further examination of the security methods available in HP-UX and Windows NT however, reveals that interoperability can exist at many levels, including the utilization of similar non-repudiation techniques. Today the prevalent core HP-UX resource protection scheme revolves around encrypted passwords and ACL for files. For more integrated and secure protection, DCE and Kerberos (a DCE derivative) methodologies are used. HP-UX can also utilize NIS file security. Today, Windows NT core security is also centered around encrypted passwords and ACL for resources, and with 3rd party software, DCE and NIS methodologies are also available. With the release of Windows NT 5.0 (Windows 2000), it has also been reported that Kerberos will be available as an alternate security paradigm. In addition, HP has released a system to provide a single source of user authentication. Thus, by utilizing 3rd party software and/or HP's security framework, a more secure cross-platform scheme for protection of resources and engineering data is possible. Security Concerns Computer security is based on four concepts: authentication, authorization, data protection and non-repudiation. Authentication refers to the process of verifying the identity of the individual who is requesting resources. For example, operating systems' logon processes provide authentication of a user to gain access to a system. Authorization provides the ability to restrict access to resources on the system by individuals or groups. This ability to tie users to certain resources and exclude them from others enables the system to be managed from a resource-based model (access control) or a role-based model (privileged users, etc.). The data protection aspect of security is essentially ensuring cryptographic algorithms and mechanisms are in place that encrypt the data, thus providing a means of keeping data confidential. Non-repudiation ensures that information was really from the indicated source and that it has not been tampered with. This validation then provides higher confidence levels in the data confidentiality process. 02/04/00 HP VISUALIZE WORKSTATIONS 1