HP Visualize J5000 hp visualize workstation - Interoperable Security for HP-UX - Page 3
Four Basic Security Concepts
 |
View all HP Visualize J5000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 3 highlights
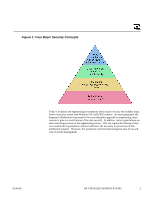
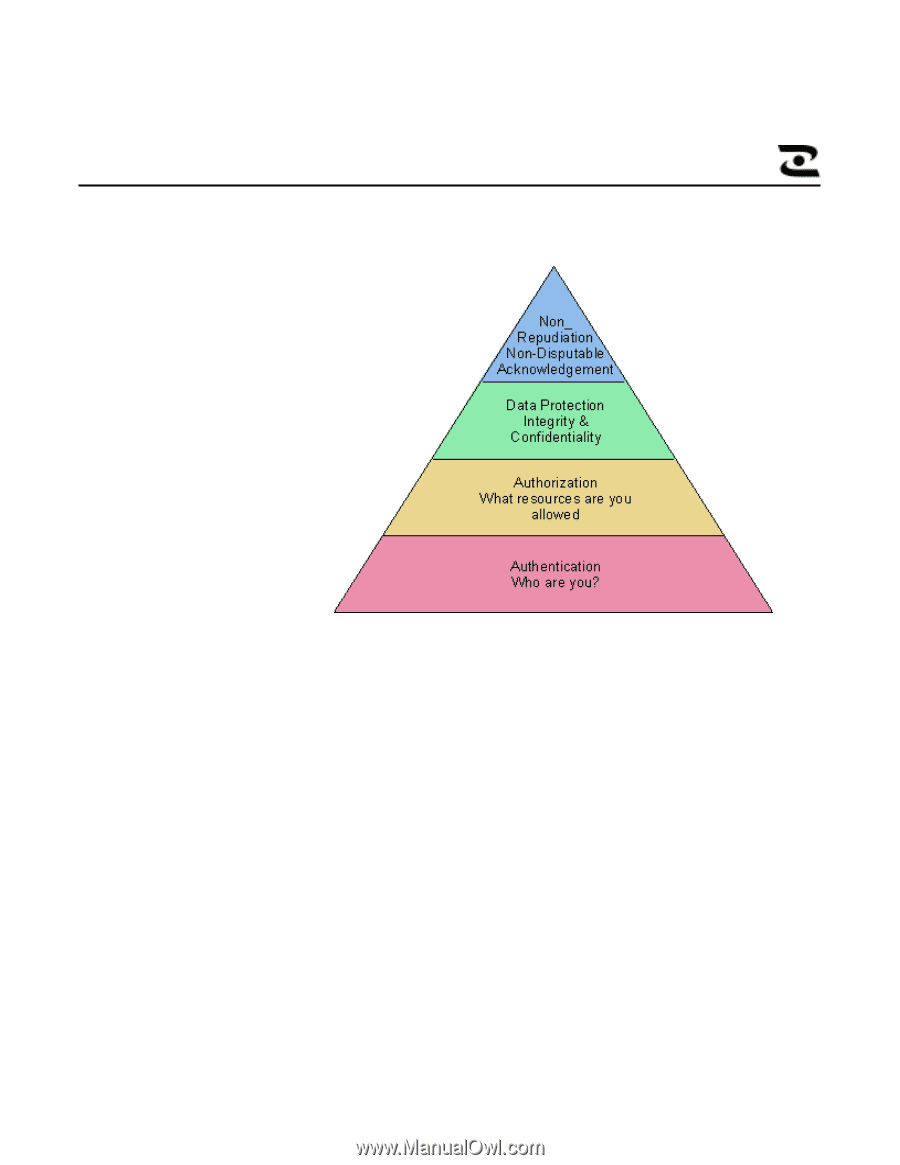
Figure 1: Four Basic Security Concepts Today's technical and engineering environments often require security that handles many levels of security across both Windows NT and UNIX systems. As more geographically dispersed collaboration is pursued in the cross discipline approach to engineering, more concern is given to ramifications of the data security. In addition, many organizations are sub-contracting portions of the engineering process. This can require the sharing of data even outside the organization's intranet and hence the necessity for protection of this intellectual property. However, this protection must be balanced against ease of use and cost of system management 02/04/00 HP VISUALIZE WORKSTATIONS 2
02/04/00
HP VISUALIZE WORKSTATIONS
2
Figure 1: Four Basic Security Concepts
Today’s technical and engineering environments often require security that handles many
levels of security across both Windows NT and UNIX systems.
As more geographically
dispersed collaboration is pursued in the cross discipline approach to engineering, more
concern is given to ramifications of the data security.
In addition, many organizations are
sub-contracting portions of the engineering process.
This can require the sharing of data
even outside the organization’s intranet and hence the necessity for protection of this
intellectual property.
However, this protection must be balanced against ease of use and
cost of system management