HP Visualize J5000 hp visualize workstation - Interoperable Security for HP-UX - Page 8
Summary
 |
View all HP Visualize J5000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 8 highlights
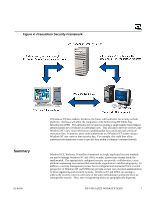
Figure 4: Praesidium Security Framework Summary 02/04/00 If Windows NT does embrace Kerberos, the future will look better for security on both platforms. Kerberos will allow the integration of the forthcoming HP Public Key Infrastructure (PKI). This infrastructure is based on issuing a single highly trusted digital identity (public key certificate) to individual users. This will allow directory services, like Windows NT's new Active Directory to publish public key certificates and certificate revocation lists. In essence, users could authenticate to a Windows NT system using a Windows NT user name or their security key. For example, this could then allow authorized subcontractors access to specific data within a company's intranet firewall. Whether DCE, Kerberos, Praesidium framework or simply duplicated security methods are used to manage Windows NT and UNIX security, a protection scheme should be implemented. The appropriately configured security can provide a collaborative, crossplatform engineering environment that protects the organization's intellectual property. In addition, a security management process that is configured and maintained from a central perspective of Windows NT and UNIX may provide a lower cost of system administration of these engineering and scientific systems. Windows NT and UNIX are starting to address the security concerns with some of the same methodologies and protocols in an interoperable manner. Thus, even if engineering teams are geographically dispersed, HP VISUALIZE WORKSTATIONS 7