HP Visualize J5000 hp visualize workstation - Interoperable Security for HP-UX - Page 4
UNIX/HP-UX View, of Security
 |
View all HP Visualize J5000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 4 highlights
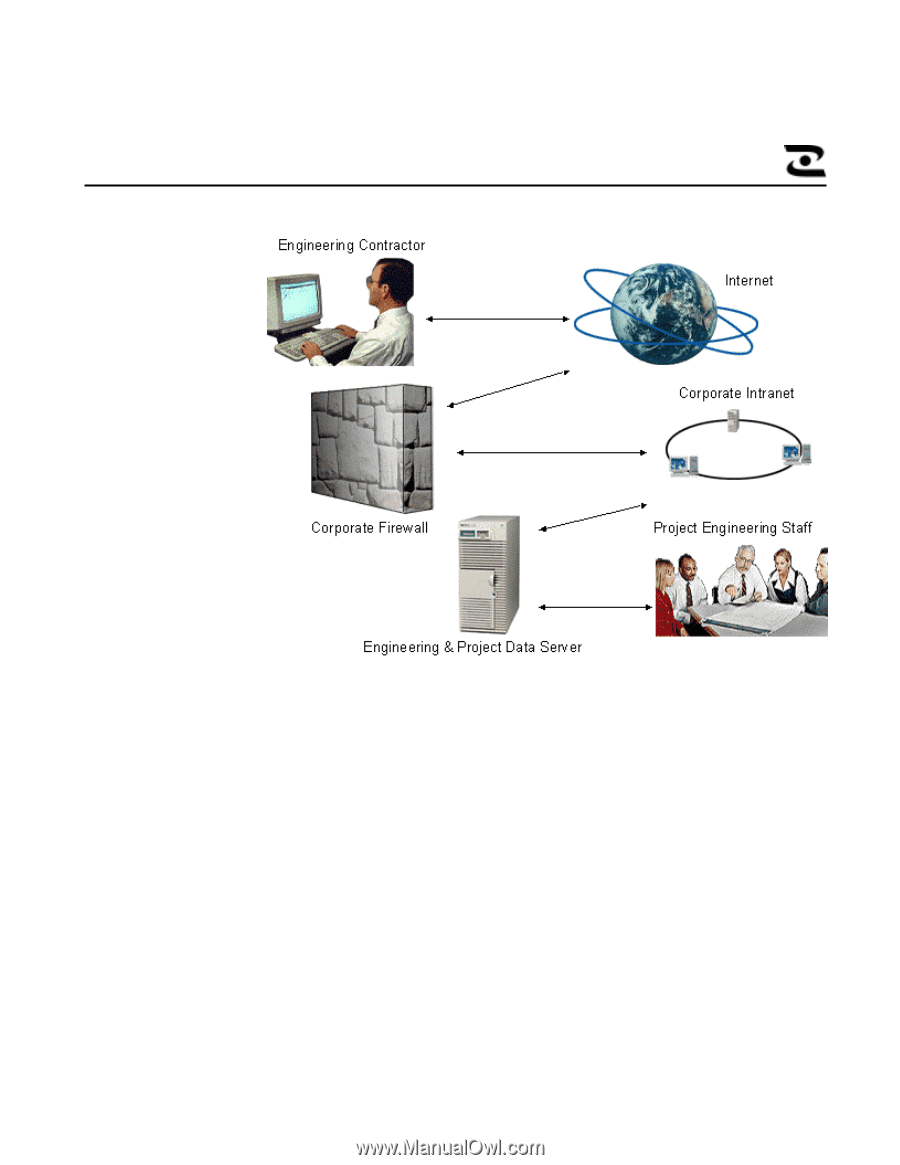
Figure 2: Collaborative Engineering Environment UNIX/HP-UX View of Security 02/04/00 An ideal security environment would be one that incorporates the security paradigms of both Windows NT and UNIX in a consistent and integrated fashion. For example, when a change in the access control or role-based model is made for a Windows NT or UNIX system, it is reflected in the other security systems. However, a balanced approached to these security paradigms, coupled with ease of use and cost of system management consideration across platforms, should be a paramount concern in the current engineering environments. A centralized security management system may assist in this integration and interoperability of security functions between the Windows NT and UNIX platforms. The UNIX operating system design was influenced to a certain extent, by a project at MIT for an "A-Level" security compliant OS called Multics. In addition, UNIX was conceived as a multi-user environment. Thus, security was considered as part of its basic design. And since UNIX resources are for the most part accessed through file I/O, UNIX security has also been historically centered around file I/O. However, despite these original design concerns, standard UNIX security is rudimentary at best. For example, most current versions of UNIX provide encrypted passwords in the password file. Unfortunately, the passwords are transmitted over the network as clear text. In addition, traditional UNIX does not address authentication of other systems on the HP VISUALIZE WORKSTATIONS 3