Netgear FVG318 FVG318 Reference Manual - Page 113
Using Digital Certificates for IKE Auto-Policy Authentication, Certificate Revocation List (CRL) - review
 |
UPC - 606449041668
View all Netgear FVG318 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 113 highlights
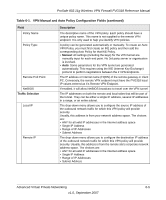
ProSafe 802.11g Wireless VPN Firewall FVG318 Reference Manual Table 6-1. VPN Manual and Auto Policy Configuration Fields (continued) Field PFS Key Group Select IKE Policy Description Perfect Forward Secrecy (PFS) improves security. While this is slower, it will ensure that a Diffie-Hellman exchange is performed for every phase 2 negotiation. • DH Group 1 (768 bit) • DH Group 2 (1024 bit) • DH Group 5 (1536 bit) The existing IKE policies are presented a drop-down list. You can also click view selected to review the settings of the selected IKE policy. This IKE policy will define the characteristics of phase 1 negotiation. Note: You must create the IKE policy before creating a VPN Auto Policy. Using Digital Certificates for IKE Auto-Policy Authentication Digital certificates are strings generated using encryption and authentication schemes that cannot be duplicated by anyone without access to the different values used in the production of the string. They are issued by Certification Authorities (CAs) to authenticate a person or a workstation uniquely. The CAs are authorized to issue these certificates by Policy Certification Authorities (PCAs), who are in turn certified by the Internet Policy Registration Authority (IPRA). The FVG318 is able to use certificates to authenticate users at the end points during the IKE key exchange process (see. The certificates can be obtained from a certificate server that an organization might maintain internally or from the established public CAs. The certificates are produced by providing the particulars of the user being identified to the CA. The information provided may include the user's name, e-mail ID, and domain name. Each CA has its own certificate. The certificates of a CA are added to the FVG318 and then can be used to form IKE policies for the user. Once a CA certificate is added to the FVG318 and a certificate is created for a user, the corresponding IKE policy is added to the FVG318. Whenever the user tries to send traffic through the FVG318, the certificates are used in place of pre-shared keys during initial key exchange as the authentication and key generation mechanism. Once the keys are established and the tunnel is set up the connection proceeds according to the VPN policy. Certificate Revocation List (CRL) Each Certification Authority (CA) maintains a list of the revoked certificates. The list of these revoked certificates is known as the Certificate Revocation List (CRL). Advanced Virtual Private Networking 6-7 v1.0, September 2007