D-Link DGS-3100-48 Product Manual - Page 165
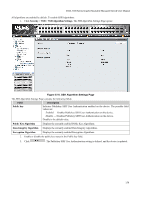
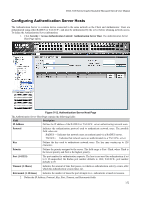
Defining SSH Algorithm Settings
 |
UPC - 790069304866
View all D-Link DGS-3100-48 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 165 highlights
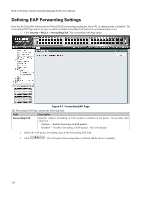
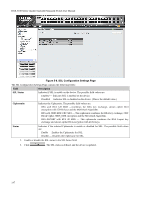
DGS-3100 Series Gigabit Stackable Managed Switch User Manual Field Description Enable - Enables SSH on the device. Disable - Disables SSH on the device. This is the default value. Port (1-65535) Displays the port number used to authenticate the SSH session. The possible field range is 165535. The field default is 22. 2. Enable or disable the SSH server status in the SSH Server Status field. 3. Define the SSH global setting port number in the Port (1-65535) field. 4. Click . The SSH configuration is defined, and the device is updated. Defining SSH Algorithm Settings This SSH Algorithm Settings Page allows network administrators to enable a public key for SSH authentication encryption. The following authentication keys are enabled for SSH: • Public Key Algorithm - Encrypt a cryptographic key pair composed of a public key and a private key. The private key is kept secret, while the public key can be distributed. The encryption keys are mathematically similar, but a private key cannot be derived from the public key. Messages encrypted with a public key can be decrypted with the matching private key. The following Public Key Algorithms are supported: - HMAC-RSA - Supports the Hash for Message Authentication Code (HMAC) mechanism utilizing the RSA encryption algorithm. - HMAC-DSA -Supports the Hash for Message Authentication Code (HMAC) Digital Signature Algorithm (DSA) encryption algorithm. • Data Integrity Algorithm - Validates message authentication information transmitted between two parties which share the same key. The following Data Integrity Algorithms are supported: - HMAC-SHA - Supports the Hash for Message Authentication Code (HMAC) Secure Hash Algorithm (SHA) mechanism. - HMAC MD5 - Supports the Hash for Message Authentication Code (HMAC) MD5 Message Digest (MD5) mechanism. • Encryption Algorithm - Generates authentication keys used to authenticate communications between different applications. The following Encryption Algorithms are supported - 3DES-CBC - Support a block size of 8 bytes (64 bits); its key size is 192 bits long. The first 8 bytes cannot be identical to the second 8 bytes, and the second 8 bytes cannot be identical to the third 8 bytes. - AES128 -Provide a block cipher that encrypts and decrypts digital information. The AES128 algorithm is capable of using cryptographic 128 keys. - AES192 - Provides a block cipher that encrypts and decrypts digital information. The AES192 algorithm is capable of using cryptographic 192 keys. - AES256 - Provide a block cipher that encrypts and decrypts digital information. The AES256 algorithm is capable of using cryptographic 256 keys. - RC4 - Supports a cipher with an up to 2048 bits key size. 149