Dell Brocade M5424 Brocade 7.1.0 Access Gateway Administrator's Guide - Page 56
Access Gateway policy enforcement matrix, Advanced Device Security policy, How the ADS policy works
 |
View all Dell Brocade M5424 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 56 highlights
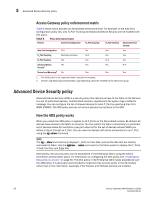
3 Advanced Device Security policy Access Gateway policy enforcement matrix Table 8 shows which policies can be enabled at the same time. For example, in the Auto Port Configuration policy row, only N_Port Trunking and Advanced Device Security can be enabled with this policy. TABLE 8 Policy enforcement matrix Policies Auto Port Configuration N_Port Grouping N_Port Trunking Advanced Device Security Auto Port Configuration N/A No Yes Yes N_Port Grouping Mutually exclusive N/A Yes Yes N_Port Trunking Yes Yes N/A Yes Advanced Device Yes Security1 Device Load Balancing2 No Yes Yes N/A Yes Yes Yes 1. The ADS policy is not supported when using device mapping. 2. Device Load Balancing and Automatic Login Balancing cannot be enabled for the same port group. Advanced Device Security policy Advanced Device Security (ADS) is a security policy that restricts access to the fabric at the AG level to a set of authorized devices. Unauthorized access is rejected and the system logs a RASLOG message. You can configure the list of allowed devices for each F_Port by specifying their Port WWN (PWWN). The ADS policy secures virtual and physical connections to the SAN. How the ADS policy works When you enable the ADS policy, it applies to all F_Ports on the AG-enabled module. By default, all devices have access to the fabric on all ports. You can restrict the fabric connectivity to a particular set of devices where AG maintains a per-port allow list for the set of devices whose PWWN you define to log in through an F_Port. You can view the devices with active connections to an F_Port using the ag --show command. NOTE The ag --show command only displays F_Ports on Core AGs, such as the AGs that are directly connected to fabric. Use the agshow --name command on the fabric switch to display the F_Ports of both the Core and Edge AGs. Alternatively, the security policy can be established in the Enterprise fabric using the Device Connection Control (DCC) policy. For information on configuring the DCC policy, see "Enabling the DCC policy on a trunk" on page 60. The DCC policy in the Enterprise fabric takes precedence over the ADS policy. It is generally recommended to implement the security policy in the AG module rather than in the main fabric, especially if the Failover and Failback policies are enabled. 36 Access Gateway Administrator's Guide 53-1002743-01