Dell DX6004S DX Object Storage Application Guide - Page 10
About Objects and Security
 |
View all Dell DX6004S manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 10 highlights
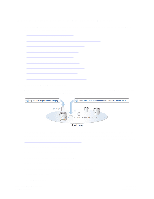
Currently, DX Storage understands only one application-level protocol, the Simple Content Storage Protocol (SCSP), which is a subset of the Hypertext Transfer Protocol, HTTP/1.1 used by web servers and browsers. While it is possible that additional access protocols will be added to DX Storage in the future, HTTP is the only protocol supported for the URI at this time. A DX Storage cluster is addressed using either the DNS name or the IP address of one of the nodes in the cluster. It doesn't matter which node is addressed initially, as long as it is accessible to the application on the network. Of course, if the addressed node has failed, or is offline for some reason, your URI might need to change. Note that it is not necessary that the node named in the URI be the same one that actually stored the object in the first place because any node can be asked to retrieve any object stored on any other node in the cluster. For unnamed objects, the UUID of an object to be retrieved from a DX Storage cluster is specified in the last component of the URI as a string of 32 case-insensitive hexadecimal digits. The length of the UUID string must always be exactly 32 characters (any leading zeros must be included). When storing an object for the first time, obviously there is no UUID assigned yet. Therefore, a WRITE request in SCSP includes just the first two components of the URI. After the data has been transferred and stored, DX Storage generates and returns a new UUID to the application. 1.8. About Objects and Security Starting with DX Storage version 5.0, you can optionally use security with named and unnamed objects. You can, for example, enable only users in a particular security realm to make changes to an object and prevent any other users from changing the object. You can apply security to buckets and to named or unnamed objects. The following figure shows a simple example of using security. In the example, the user Joe has access to the docs bucket where he can create named objects and user Jim has access to the videos bucket. Neither Joe nor Jim can write named objects to any other domain in the cluster (cloud.com). 1.8.1. The Basics of DX Storage Security DX Storage's security model uses the standard two-part approach of: • Authentication: DX Storage uses standard Digest Access Authentication as discussed in RFC 2617 to create one-way cryptographic hash algorithms to obscure identity information over the Internet while allowing a client (for example, a web browser) and the DX Storage server to exchange enough information to consummate authentication. DX Storage validates user names and passwords from a security realm, which is discussed in the next section. • Authorization: Provided a user authenticates successfully, the user's privileges are derived from the authorization specification associated with the object the user attempts to access. The authorization specification is discussed in the next section. Copyright © 2010 Caringo, Inc. All rights reserved 5 Version 5.0 December 2010