Dell PowerVault TL2000 Dell PowerVault ML6000 Encryption Key Manager User's - Page 28
Two-Server Configurations, Identical configurations, Separate configurations - user manual
 |
View all Dell PowerVault TL2000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 28 highlights
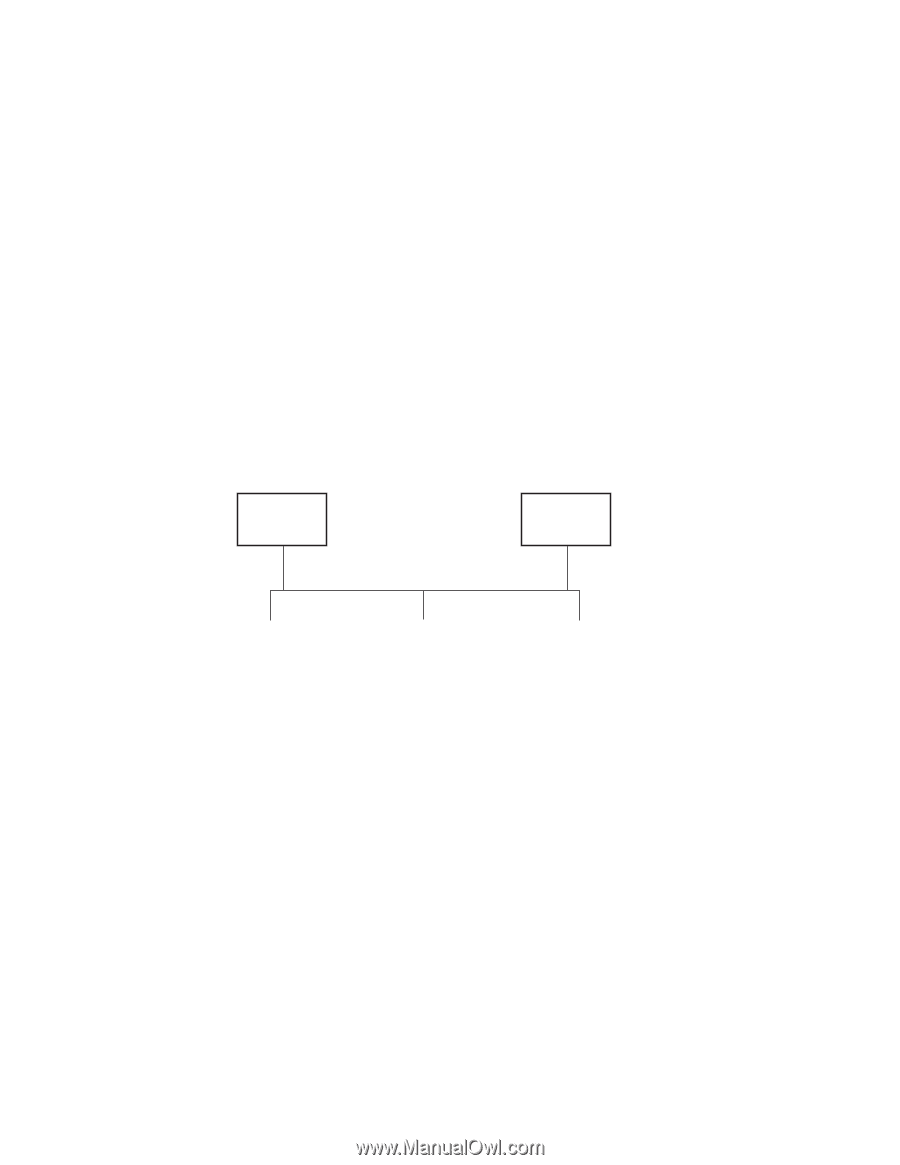
Two-Server Configurations A two-server configuration is recommended. This Encryption Key Manager configuration will automatically failover to the secondary key manager should the primary be inaccessible for any reason. Note: When different Encryption Key Manager servers are used to handle requests from the same set of tape drives, the information in the associated keystores MUST be identical. This is required so that regardless which key manager server is contacted, the necessary information is available to support requests from the tape drives. Identical configurations: In an environment with two Encryption Key Manager servers having identical configurations, such as those shown in Figure 2-5, processing will automatically failover to the secondary key manager should the primary go down. In such a configuration it is essential that the two key manager servers be synchronized. Updates to the configuration file and drive table of one key manager server can be duplicated on the other automatically using the sync command, but updates to one keystore must be copied to the other using methods specific to the keystore(s) being used. The keystores and key groups XML file must be copied manually. Refer to "Synchronizing Data Between Two Key Manager Servers" on page 4-2 for more information. | Primary Key Store Encryption Drive Table Key Manager Config File Key Groups = = = = Key Store Drive Table Config File Key Groups Secondary Encryption Key Manager a14m0254 Tape Library Tape Library Tape Library A B C | | Figure 2-5. Two Servers with Shared Configurations | Separate configurations: Two Encryption Key Manager servers may share a common keystore and drive table yet have two different configuration files and two different sets of key groups defined in their XML files. The only requirement is that the keys used to serve the common tape drives must be the same for each server. This allows each key manager server to have its own set of properties. In this type of configuration, shown in Figure 2-6 on page 2-9, only the drive table should be synchronized between key manager servers. (Refer to "Synchronizing Data Between Two Key Manager Servers" on page 4-2 for more information.) Be sure to specify sync.type = drivetab (do not specify config or all) to prevent the configuration files from being overwritten. Note: There is no way to partially share the configuration between servers. 2-8 Dell Encryption Key Mgr User's Guide