Dell PowerVault TL2000 Dell PowerVault ML6000 Encryption Key Manager User's - Page 93
Audit Points in the Encryption Key Manager, Audit Record Attributes, Authentication event
 |
View all Dell PowerVault TL2000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 93 highlights
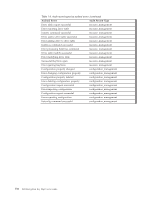
bracket (]) indented two (2) spaces. The number of lines for each audit record varies based on the audit record type and the additional attribute information that is provided with the audit record. The timestamp for the audit records is based on the system clock of the system on which the Encryption Key Manager is running. If these records are to be correlated based on timestamp with events occurring on other systems, some type of time synchronization should be used to ensure that the clocks of the various systems in the environment are synchronized to an acceptable level of accuracy. Audit Points in the Encryption Key Manager The Encryption Key Manager can write audit records, based on configuration, for many events that occur during the processing of requests. In this section, the set of events that can be audited is described along with the audit record configuration category, which must be enabled in order for these audit records to be written to the audit files (see Table 7-1). Table 7-1. Audit record types that the Encryption Key Manager writes to audit files Audit Record Type Authentication Data Synchronization Runtime Resource Management Configuration Management Audit Type authentication data_synchronization runtime resource_management configuration_management Description Used to log authentication events Used to log data synchronization processing Used to log various important processing events which occur within the Encryption Key Manager server while handling requests Used to log changes to how resources are configured to the Encryption Key Manager Used to log changes to the configuration of the Encryption Key Manager server Audit Record Attributes The following lists show the attributes available to each of the audit record types. Authentication event The format for these records is: Authentication event:[ timestamp=timestamp event source=source outcome=outcome event type=SECURITY_AUTHN message=message authentication type=type users=users ] Note that the message value only appears if information for it is available. Chapter 7. Audit Records 7-5