Ricoh Aficio MP 3350B Security Target - Page 58
O. AUDIT, Audit
 |
View all Ricoh Aficio MP 3350B manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 58 highlights
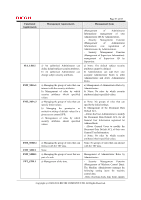
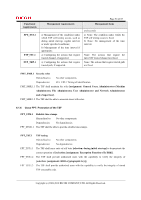
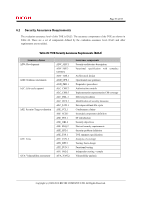
FIA_UID.2 FIA_USB.1 FMT_MSA.1 FMT_MSA.3 FMT_MTD.1 FMT_SMF.1 FMT_SMR.1 FPT_STM.1 FPT_TST.1 FTP_ITC.1 FTP_TRP.1 X X X Page 58 of 83 X X X X X X X X X 6.3.2 Tracing Validity This chapter describes how the TOE security objectives are accomplished by the TOE security functional requirements corresponding to the TOE security objectives in Table 23. O. AUDIT Audit The following are the rationale for the functional requirements that correspond to O.AUDIT in Table 23 being appropriate to satisfy O.AUDIT. a) Record audit logs To accomplish O.AUDIT, it is necessary to record the performance of security functions as audit logs. For this, FAU_GEN.1 generates the audit information when starting and ending Audit Function, when performing the Identification and Authentication Function, when users operate the protected assets, when encrypting the protected assets, and when performing the major management functions. It also records the date and time of the event, type of event, subject identity and the outcome of the event. b) Provide Audit Function To accomplish O.AUDIT, it is necessary to provide only the Machine Administrator with access to audit logs and in a format that can be audited. For this, FAU_SAR.1 makes it possible for the Machine Administrator to verify audit logs, and FAU_SAR.2 prohibits the persons other than the Machine Administrator to read audit logs. c) Protect audit logs To accomplish O.AUDIT, objectives to adequately protect audit logs are necessary. For this, FAU_STG.4 protects audit logs from the unauthorised deletion and prevents the unauthorised tampering. If the auditable events occur and the audit log files are full, FAU_STG.4 also prevents the latest audit logs from being lost by writing the new audit log over the audit log that has the oldest time stamp. d) Time of reliable events occurrence To accomplish O.AUDIT, it is necessary to record the accurate time of events occurrence to adequately Copyright (c) 2009,2010 RICOH COMPANY, LTD. All Rights Reserved.