Ricoh Aficio MP 3350B Security Target - Page 77
SF.NET_PROT Network Communication Data Protection Function, 1.7.1, Use of Web Service Function
 |
View all Ricoh Aficio MP 3350B manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 77 highlights
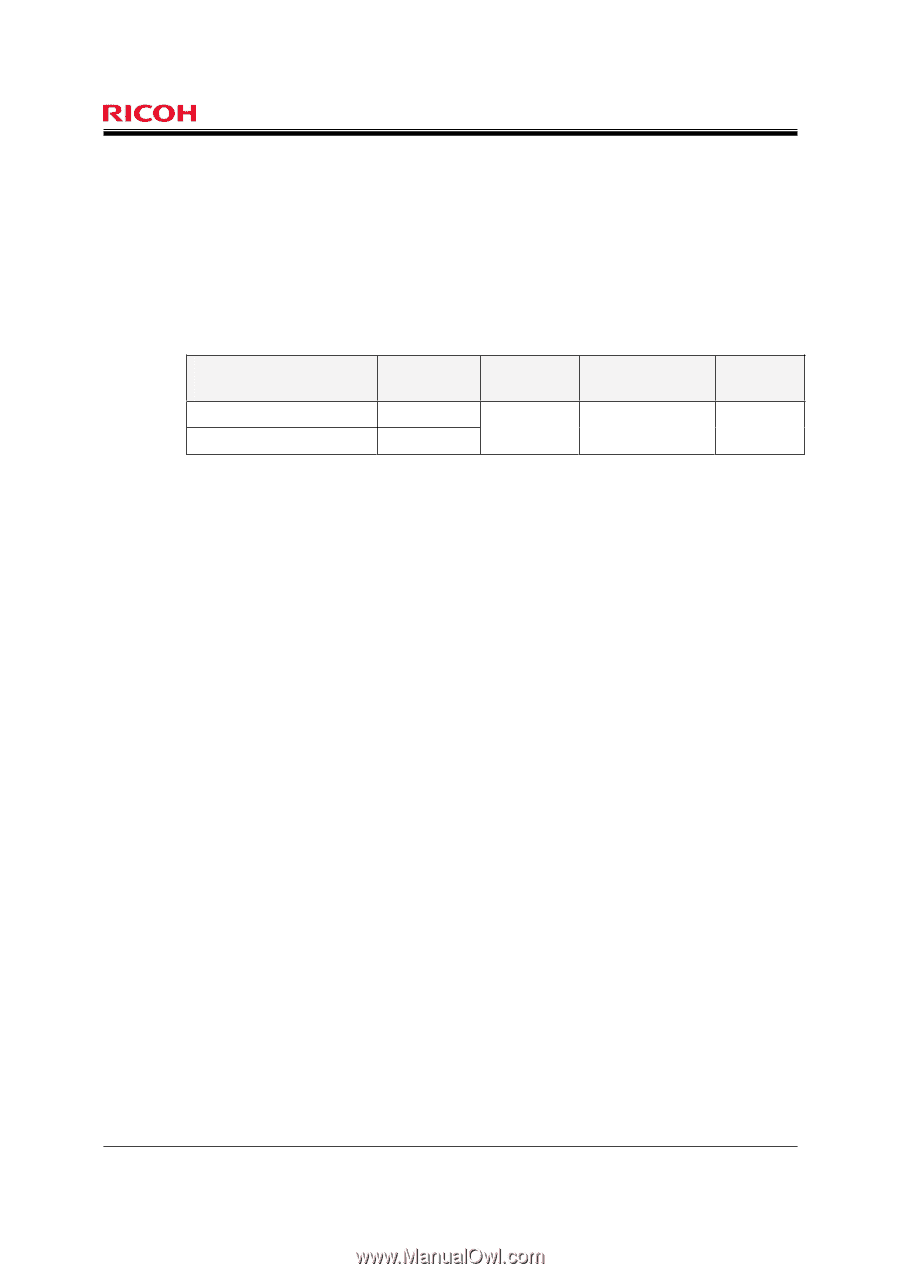
Page 77 of 83 The HDD encryption keys are generated by the Machine Administrator. If the login user is the Machine Administrator, the TOE provides the screen to generate the HDD encryption keys from the Operation Panel. When the Machine Administrator gives the instruction to generate HDD encryption key from the Operation Panel, the TOE generates the 256-bit HDD encryption key with the encryption key generation algorithm TRNG complying with the Standard BSI-AIS31, and when writing the data on the HDD/reading the data from the HDD, it performs the encryption operations shown in Table 34. Table 34: List of Encryption Operation on Stored Data on HDD Triggers of encryption operation Writing data on HDD Reading data from HDD Encryption operations Encrypt Decrypt Standard FIPS197 Encryption algorithm AES Key size 256 bits The HDD encryption keys can be also printed. If the login user is the Machine Administrator, the TOE provides the Machine Administrator with the screen to print the HDD encryption keys from the Operation Panel. The printed encryption keys are used to restore the encryption keys in case the encryption keys in the TOE are unavailable. In addition, the TOE verifies that the encryption function of Ic Hdd operates normally at start-up and verifies the integrity of the HDD encryption keys. If the TOE is not able to verify the integrity of the HDD encryption keys, it indicates that the HDD encryption keys are changed. From the above, FCS_CKM.1 (Cryptographic key generation), FCS_COP.1 (Cryptographic operation), FMT_MTD.1 (Management of TSF data) and FPT_TST.1 (TSF testing) are accomplished. 7.1.7 SF.NET_PROT Network Communication Data Protection Function Network Communication Data Protection Function protects Document Data and Print Data on the Internal Networks from leakage, and detects tampering of Document Data and Print Data. The following are the explanations of each functional item in "SF.NET_PROT Network Communication Data Protection Function" and their corresponding security functional requirements. 7.1.7.1 Use of Web Service Function from Client PC When receiving requests to use the Web Service Function from a client PC, the TOE communicates with the client PC using the SSL protocol as a trusted path. From the above, FTP_TRP.1 (Trusted path) is accomplished. 7.1.7.2 Printing and Faxing from Client PC When receiving requests for printing or fax transmission from a client PC, the TOE communicates with the client PC using the SSL protocol as a trusted path. From the above, FTP_TRP.1 (Trusted path) is accomplished. Copyright (c) 2009,2010 RICOH COMPANY, LTD. All Rights Reserved.