Ricoh Aficio MP C305 Security Target - Page 73
O.CONF.NO_ALT Protection of TSF confidential data alteration, O.USER.AUTHORIZED User identification
 |
View all Ricoh Aficio MP C305 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 73 highlights
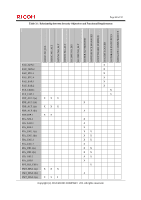
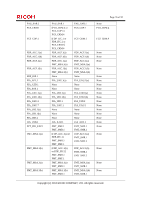
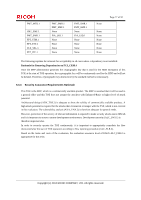
Page 72 of 91 (4) Use trusted channels for sending or receiving TSF confidential data. The TSF confidential data sent and received by the TOE via the LAN are protected by FTP_ITC.1. By satisfying FMT_MTD.1, FMT_SMF.1, FMT_SMR.1 and FTP_ITC.1, which are the security functional requirements for these countermeasures, O.CONF.NO_DIS is fulfilled. O.CONF.NO_ALT Protection of TSF confidential data alteration O.CONF.NO_ALT is the security objective to allow only users who can maintain the security to alter the TSF confidential data. To fulfil this security objective, it is required to implement the following countermeasures. (1) Management of the TSF confidential data. FMT_MTD.1 allows the MFP administrator and applicable normal user to operate the login password of normal user. A supervisor is allowed to operate the login password of supervisor. The supervisor and applicable MFP administrator are allowed to operate the login password of administrator. The MFP administrator is only allowed to operate the audit log and newly create an HDD cryptographic key. (2) Specification of the Management Function. FMT_SMF.1 performs the required Management Functions for Security Function. (3) Specification of the roles. FMT_SMR.1 maintains the users who have the privileges. (4) Use trusted channels for sending or receiving TSF confidential data. The TSF confidential data sent and received by the TOE via the LAN are protected by FTP_ITC.1. By satisfying FMT_MTD.1, FMT_SMF.1, FMT_SMR.1 and FTP_ITC.1, which are the security functional requirements for these countermeasures, O.CONF.NO_ALT is fulfilled. O.USER.AUTHORIZED User identification and authentication O.USER.AUTHORIZED is the security objective to restrict users in accordance with the security policies so that only valid users can use the TOE functions. As for normal users, the MFP administrator, and a supervisor, who all access the TOE from the Operation Panel or from the client PC over a network, the security policies of the authentication failure handling and verification of secrets need to be augmented. To fulfil this security objective, it is required to implement the following countermeasures. (1) Identify and authenticate the users prior to the TOE use. FIA_UID.1(a) and FIA_UAU.1(a) identify and authenticate the persons who attempt to use the TOE from the Operation Panel or client computer on the network by the Basic Authentication. FIA_UID.1(b) and FIA_UAU.1(b) identify and authenticate the persons by the Basic Authentication if the person who attempts to use the TOE from the Operation Panel or client computer on the network is the MFP administrator or supervisor, and if the person is the normal user, the External Authentication is used for the identification and authentication. FIA_UID.2 identifies the person who attempts to use the TOE from the interface for RC Gate communication, and FIA_UAU.2 authenticates RC Gate. (2) Allow the successfully identified and authenticated user to use the TOE. FIA_ATD.1 and FIA_USB.1 manage the access procedures to the protected assets of the users who are defined in advance, and associate the users who are successfully identified and authenticated with the access procedures. Copyright (c) 2012 RICOH COMPANY, LTD. All rights reserved.