ZyXEL ES-2024A User Guide - Page 174
AAA Screens
 |
View all ZyXEL ES-2024A manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 174 highlights
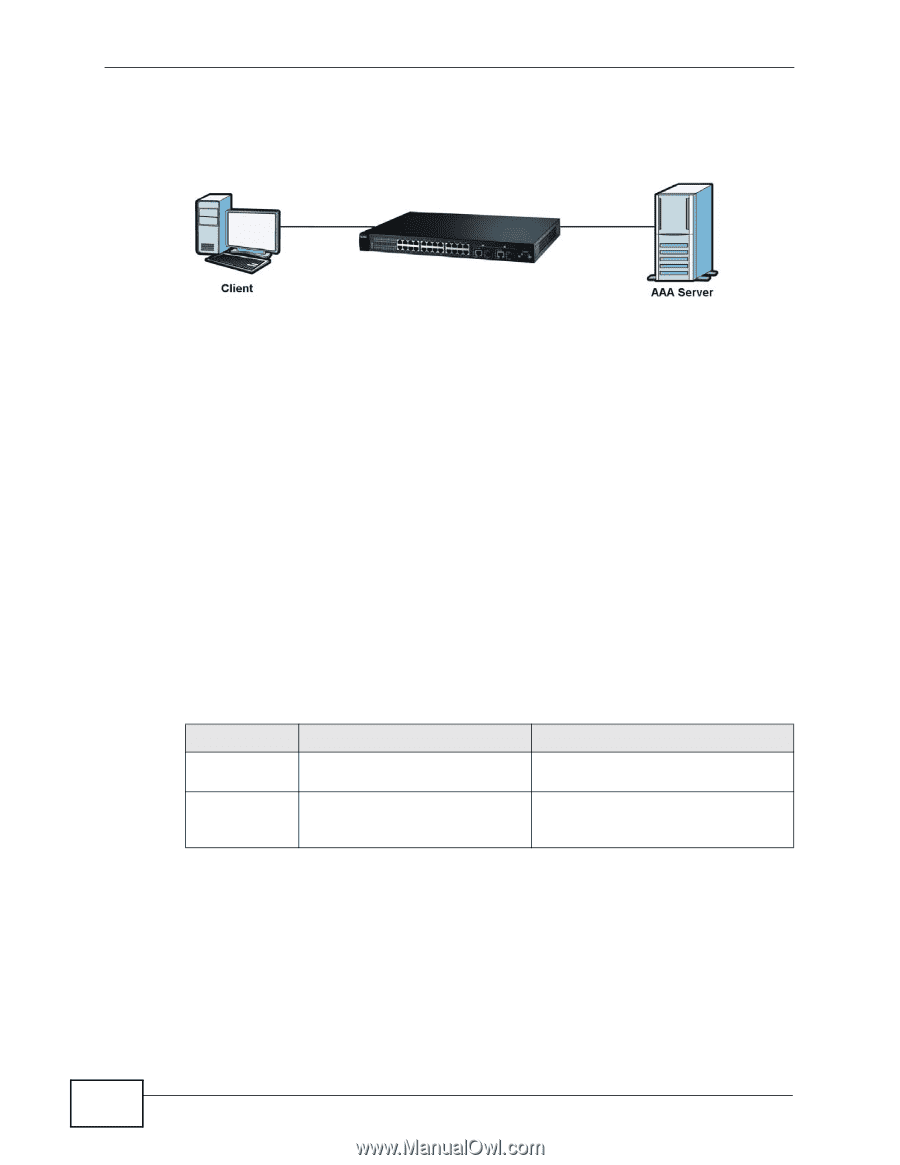
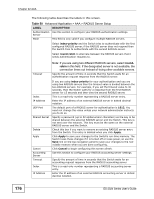
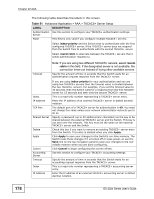
Chapter 22 AAA 22.1.2 on page 174) as external authentication, authorization and accounting servers. Figure 89 AAA Server 22.1.1 Local User Accounts By storing user profiles locally on the Switch, your Switch is able to authenticate and authorize users without interacting with a network AAA server. However, there is a limit on the number of users you may authenticate in this way (See Chapter 29 on page 233). 22.1.2 RADIUS and TACACS+ RADIUS and TACACS+ are security protocols used to authenticate users by means of an external server instead of (or in addition to) an internal device user database that is limited to the memory capacity of the device. In essence, RADIUS and TACACS+ authentication both allow you to validate an unlimited number of users from a central location. The following table describes some key differences between RADIUS and TACACS+. Table 49 RADIUS vs. TACACS+ RADIUS Transport Protocol UDP (User Datagram Protocol) Encryption Encrypts the password sent for authentication. TACACS+ TCP (Transmission Control Protocol) All communication between the client (the Switch) and the TACACS server is encrypted. 22.2 AAA Screens To enable authentication, accounting or both on the Switch. First, configure your authentication server settings (RADIUS, TACACS+ or both) and then set up the authentication priority and accounting settings. 174 ES-2024 Series User's Guide