Dell PowerConnect W-IAP3WN Dell Instant 6.1.3.1-3.0.0.0 User Guide - Page 129
Instant Firewall
 |
View all Dell PowerConnect W-IAP3WN manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 129 highlights
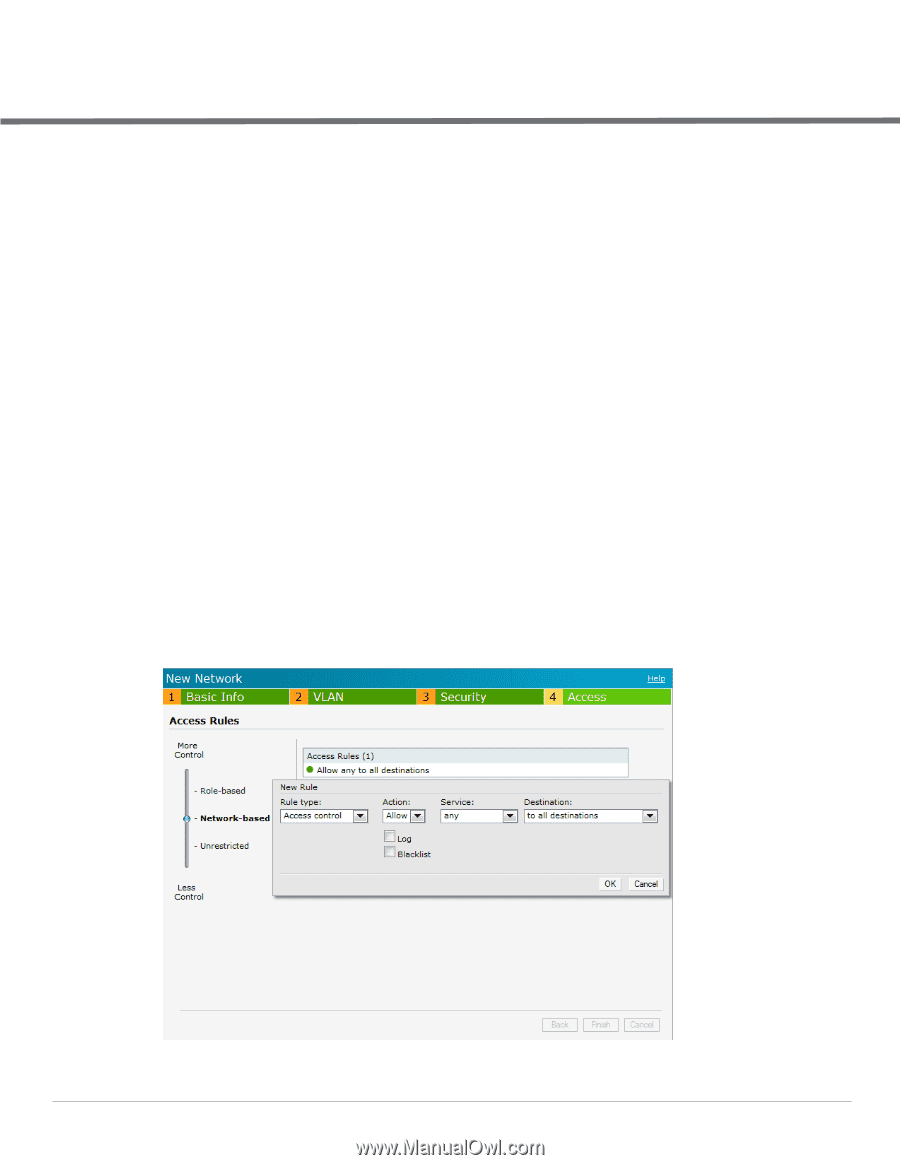
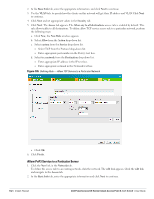
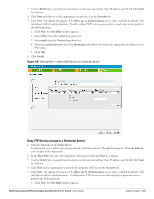
Chapter 12 Instant Firewall A firewall is a system designed to prevent unauthorized Internet users from accessing the private network connected to the Internet. It defines access rules and monitors all data entering or leaving the network and blocks the data that does not satisfy the specified security policies. Dell Instant implements the Instant Firewall feature that uses a simplified firewall policy language. An administrator can define the firewall policies on an SSID or wireless network such as the Guest network or an Employee network. At the end of authentication, these policies are uniformly applied to users connected to that network. The Instant Firewall gives the flexibility to limit packets or bandwidth available to particular class of users. Instant Firewall treats packets based on the first rule matched. 1. In the Networks tab, click the New link. The New Network window appears. 2. Navigate to Access tab to specify the access rules for the network. 3. Slide to Network-based using the scroll bar and click New to add a new rule. The New Rule window consists of the following options: Rule type- Select the rule type (Access control, VLAN assignment) from the drop-down list. Action- Select Allow or Deny from the drop-down list to allow or deny traffic with the specified service type and destination. Log- Select this checkbox if you want a log entry to be created when this rule is triggered. Instant firewall supports firewall based logging function. Firewall logs on IAP are generated as syslog messages. Blacklist- Select this checkbox if you want the client to be blacklisted when this rule is triggered. The blacklisting will last for the duration specified as Auth failure blacklist time on the Blacklisting tab of the PEF window. See "Client Blacklisting" on page 193 for more information. Figure 104 Access Tab - Instant Firewall Settings Dell PowerConnect W-Series Instant Access Point 6.1.3.1-3.0.0.0 | User Guide Instant Firewall | 129