HP Brocade 8/12c Fabric OS Encryption Administrator's Guide - Page 200
Multiple paths, one DEK cluster, and two HA clusters
 |
View all HP Brocade 8/12c manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 200 highlights
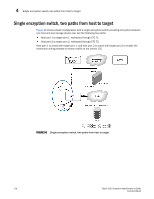
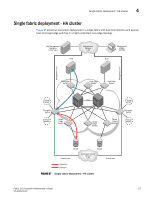
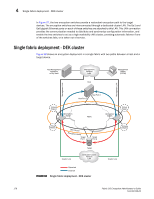
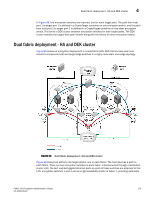
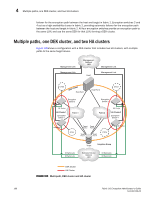
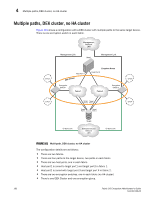
4 Multiple paths, one DEK cluster, and two HA clusters failover for the encryption path between the host and target in fabric 1. Encryption switches 2 and 4 act as a high availability cluster in fabric 2, providing automatic failover for the encryption path between the host and target in fabric 2. All four encryption switches provide an encryption path to the same LUN, and use the same DEK for that LUN, forming a DEK cluster. Multiple paths, one DEK cluster, and two HA clusters Figure 100shows a configuration with a DEK cluster that includes two HA clusters, with multiple paths to the same target device. Management Link Management Link Management Network LAN Host Management Link Management Link CTC2 DEK Cluster Host Port 1 Encryption Switch 2 GE Port(s) HA Cluster1 Encryption Switch 1 Fabric1 Host Port 2 CTC3 Encryption Switch 3 Fabric2 GE Port(s) HA Cluster2 Encryption Switch 4 GE Port(s) CTC1 Target Target Port 2 Port 3 Target Port 1 Target Port 4 CTC4 GE Port(s) IO Sync Link IO Sync Link Target Ecryption Group Dedicated Cluster Network LAN IO Sync Link IO Sync Link DEK Cluster HA Cluster FIGURE 100 Multi-path, DEK cluster and HA cluster 180 Fabric OS Encryption Administrator's Guide 53-1002159-03