HP Jetdirect 610n HP Jetdirect Security Guidelines - Page 11
Recommended Security Deployments: SET 1, picasso, ht=ether, vm=rfc1048, ha=0001E6123456
 |
View all HP Jetdirect 610n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 11 highlights
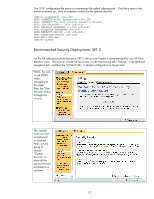
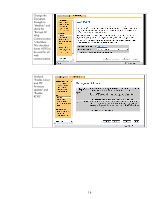
Recommended Security Deployments: SET 1 The HP Jetdirect products denoted by SET 1 do not have any cryptographic security capability. As a result, a BOOTP/TFTP configuration is recommended as we can specify several control parameters via the TFTP configuration file. This configuration file allows for a great deal of power with very little administration overhead once configured. Many customers associate BOOTP/TFTP with UNIX or Linux environments; however, there are many free BOOTP and TFTP servers for Windows and setup is fairly easy. An example UNIX configuration will be provided here. picasso:\ :hn:\ :ht=ether:\ :vm=rfc1048:\ :ha=0001E6123456:\ :ip=192.168.40.39:\ :sm=255.255.255.0:\ :gw=192.168.40.1:\ :lg=192.168.40.3:\ :T144="hpnp/picasso.cfg":\ :T151="BOOTP-ONLY": This configuration provides the following: • Syslog server: 192.168.40.3 • TFTP configuration file: picasso.cfg under the subdirectory of "hpnp" of the TFTP daemon's home directory • Forces HP Jetdirect to remain with BOOTP and not transition to DHCP if a BOOTP server is unavailable. An example of the contents of the TFTP configuration file picasso.cfg: # Allow subnet 192.168.40.0 access allow: 192.168.40.0 255.255.255.0 # # Disable Telnet telnet-config: 0 # # Disable the embedded Web server ews-config: 0 # # disable unused protocols ipx/spx: 0 dlc/llc: 0 ethertalk:0 # # Set a password passwd: Security4Me3 # # Disable SNMP # use with caution - breaks SNMP management tools snmp-config:0 # # if SNMP must be enabled, comment out the "snmp-config" command and # uncomment out the following: # set-community-name: Security4Me3 # get-community-name: notpublic # default-get-community: 0 # # parameter file parm-file: hpnp/pjlprotection # 11