HP Jetdirect 610n HP Jetdirect Security Guidelines - Page 28
Recommended Security Deployments: SET 4, Select All IP
 |
View all HP Jetdirect 610n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 28 highlights
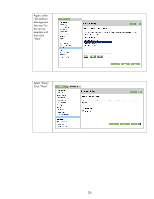
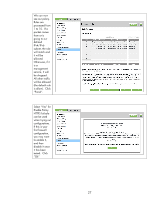
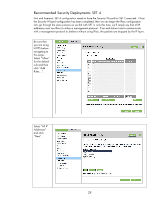
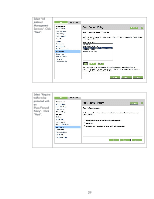
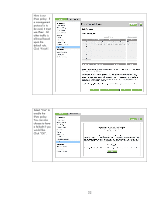
Recommended Security Deployments: SET 4 First and foremost, SET 4 configuration needs to have the Security Wizard for SET 2 executed. Once the Security Wizard configuration has been completed, then we can begin the IPsec configuration. Let's go through the same process as we did with SET 3, only this time, we'll simply say that all IP addresses must use IPsec to utilize a management protocol. If an end station tries to communicate with a management protocol to Jetdirect without using IPsec, the packets are dropped by the IP layer. Be sure that you are using HTTPS before navigating to this page. Select "Allow" for the default rule and then click "Add Rules...". Select "All IP Addresses" and click "Next". 28
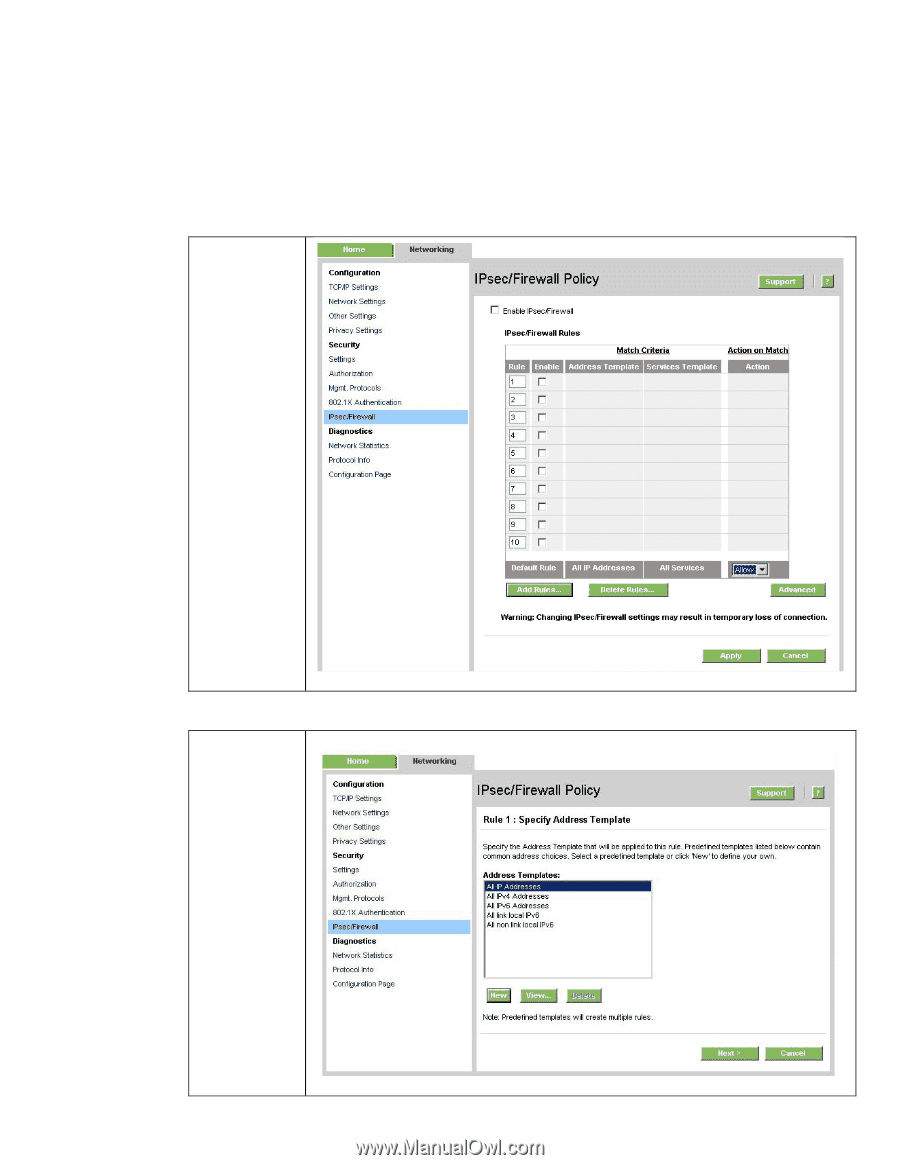
Recommended Security Deployments: SET 4
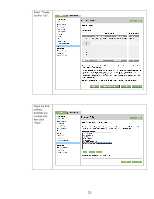
First and foremost, SET 4 configuration needs to have the Security Wizard for SET 2 executed.
Once
the Security Wizard configuration has been completed, then we can begin the IPsec configuration.
Let’s go through the same process as we did with SET 3, only this time, we’ll simply say that all IP
addresses must use IPsec to utilize a management protocol.
If an end station tries to communicate
with a management protocol to Jetdirect without using IPsec, the packets are dropped by the IP layer.
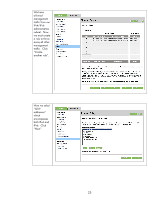
Be sure that
you are using
HTTPS before
navigating to
this page.
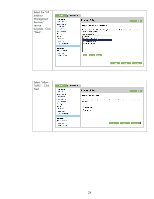
Select “Allow”
for the default
rule and then
click “Add
Rules…”.
Select “All IP
Addresses”
and click
“Next”.
28