HP Jetdirect 610n HP Jetdirect Security Guidelines - Page 18
Recommended Security Deployments: SET 3, the Security Wizard configuration has been completed
 |
View all HP Jetdirect 610n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 18 highlights
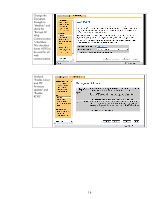
Configuration Review Configuration review. Click "Finish" to set the configuration. Recommended Security Deployments: SET 3 First and foremost, SET 3 configuration needs to have the Security Wizard for SET 2 executed. Once the Security Wizard configuration has been completed, then we can begin the Firewall configuration. A sample Firewall configuration is shown where the management protocols are restricted to a specific IP subnet range: 18
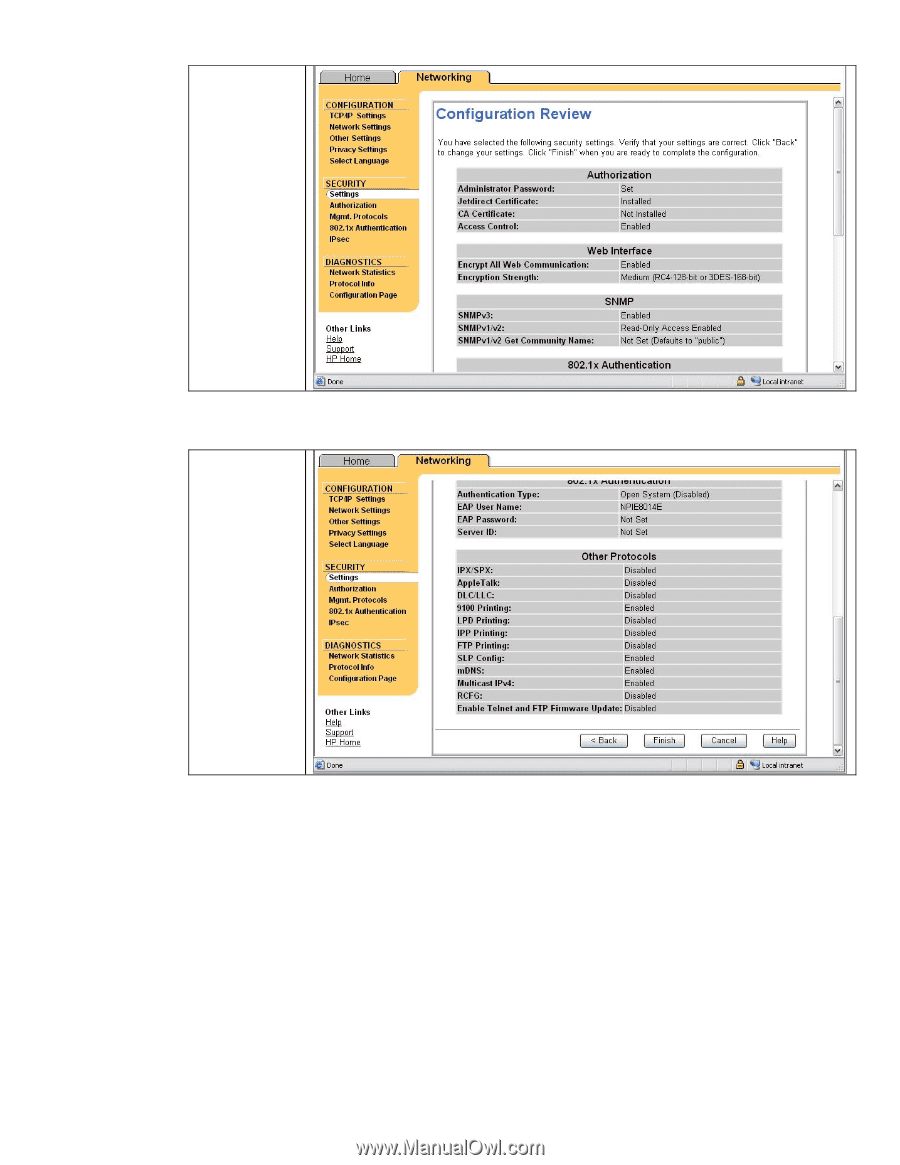
Configuration
Review
Configuration
review.
Click
“Finish” to set
the
configuration.
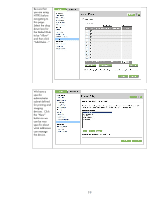
Recommended Security Deployments: SET 3
First and foremost, SET 3 configuration needs to have the Security Wizard for SET 2 executed.
Once
the Security Wizard configuration has been completed, then we can begin the Firewall configuration.
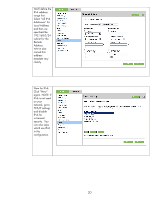
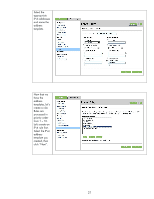
A sample Firewall configuration is shown where the management protocols are restricted to a specific
IP subnet range:
18