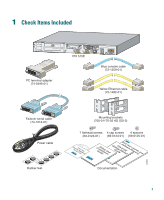
Cisco PIX-515E Quick Start Guide - Page 6
Example Configurations, DMZ Configuration - vpn configuration
 |
View all Cisco PIX-515E manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 6 highlights
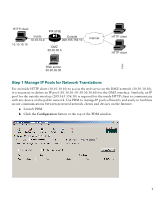
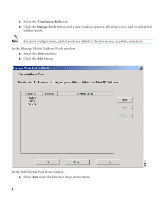
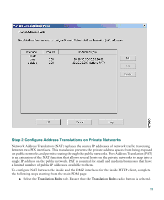
Step 4 To access the Startup Wizard, use the PC connected to the switch or hub and enter the URL https://192.168.1.1/startup.html into your Internet browser. Note Remember to add the "s" in "https" or the connection fails. HTTPS (HTTP over SSL) provides a secure connection between your browser and the PIX 515E. Step 5 Step 6 Leave both the username and password boxes empty. Press Enter. Select Yes to accept the certificates and follow the instructions in the Startup Wizard to set up your PIX 515E. For online Help, click the Help button at the bottom of the Startup Wizard window. 4 Example Configurations The following section provides configuration examples for two common PIX 515E configuration scenarios: hosting a web server on a DMZ network and establishing a site-to-site VPN connection with other business partners or remote offices. Use these examples to set up your network. Substitute network addresses and apply additional policies as needed. DMZ Configuration A demilitarized zone (DMZ) is a neutral zone between private (inside) and public (outside) networks. A DMZ allows you to have a presence on the public Internet, while protecting private network resources that are accessed by users on the public Internet; for example, mail servers or web servers. The illustration below shows a sample network topology that is common to most DMZ implementations using the PIX 515E, in which the web server is on the DMZ interface. HTTP clients from the inside and the outside networks are able to access the web server securely. In the illustration below, an HTTP client (10.10.10.10) on the inside network initiates HTTP communications with the DMZ web server (30.30.30.30). HTTP access to the DMZ web server is provided for all clients on the Internet; all other communications are denied. The network is configured such that the range of available IP addresses on the DMZ interface are between 30.30.30.50-30.30.30.60. There are two publicly routable IP addresses available, one for the PIX 515E outside interface (209.165.156.10) and one for the translated DMZ server (209.165.156.11). Because the DMZ server is located on a private DMZ network, it is necessary to translate its private IP address to a public (routable) IP address. This public address allows external clients HTTP access to the DMZ server as though it was located on the Internet. Use PDM to quickly configure your PIX 515E for secure communications between HTTP clients and web servers. 6