Dynex DX-NNBC User Manual (English) - Page 16
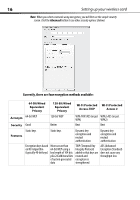
Currently, there are four encryption methods available, Advanced
 |
UPC - 600603119064
View all Dynex DX-NNBC manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 16 highlights
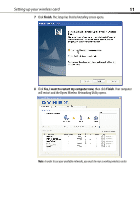
16 Setting up your wireless card Note: When you select a network using encryption, you will first see the simple security screen. Click the Advanced button to see other security options (below). Currently, there are four encryption methods available: 64-Bit Wired Equivalent Privacy 128-Bit Wired Equivalent Privacy Wi-Fi Protected Wi-Fi Protected Access-TKIP Access 2 Acronym 64-bit WEP 128-bit WEP WPA-TKIP/AES (or just WPA2-AES (or just WPA) WPA2) Security Good Better Best Best Static keys Features Static keys Dynamic key encryption and mutual authentication Dynamic key encryption and mutual authentication Encryption keys based More secure than TKIP (Temporal Key AES (Advanced on RC4 algorithm 64-bit WEP using a Integrity Protocol) Encryption Standard) (typically 40-bit keys) key length of 104 bits added so that keys are does not cause any plus 24 additional bits rotated and throughput loss of system generated encryption is data strengthened