Fujitsu ST5030D User's Guide - Page 24
Security Functions Of Application Buttons, Setting Up The Security Panel, Passwords
 |
UPC - 611343041447
View all Fujitsu ST5030D manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 24 highlights
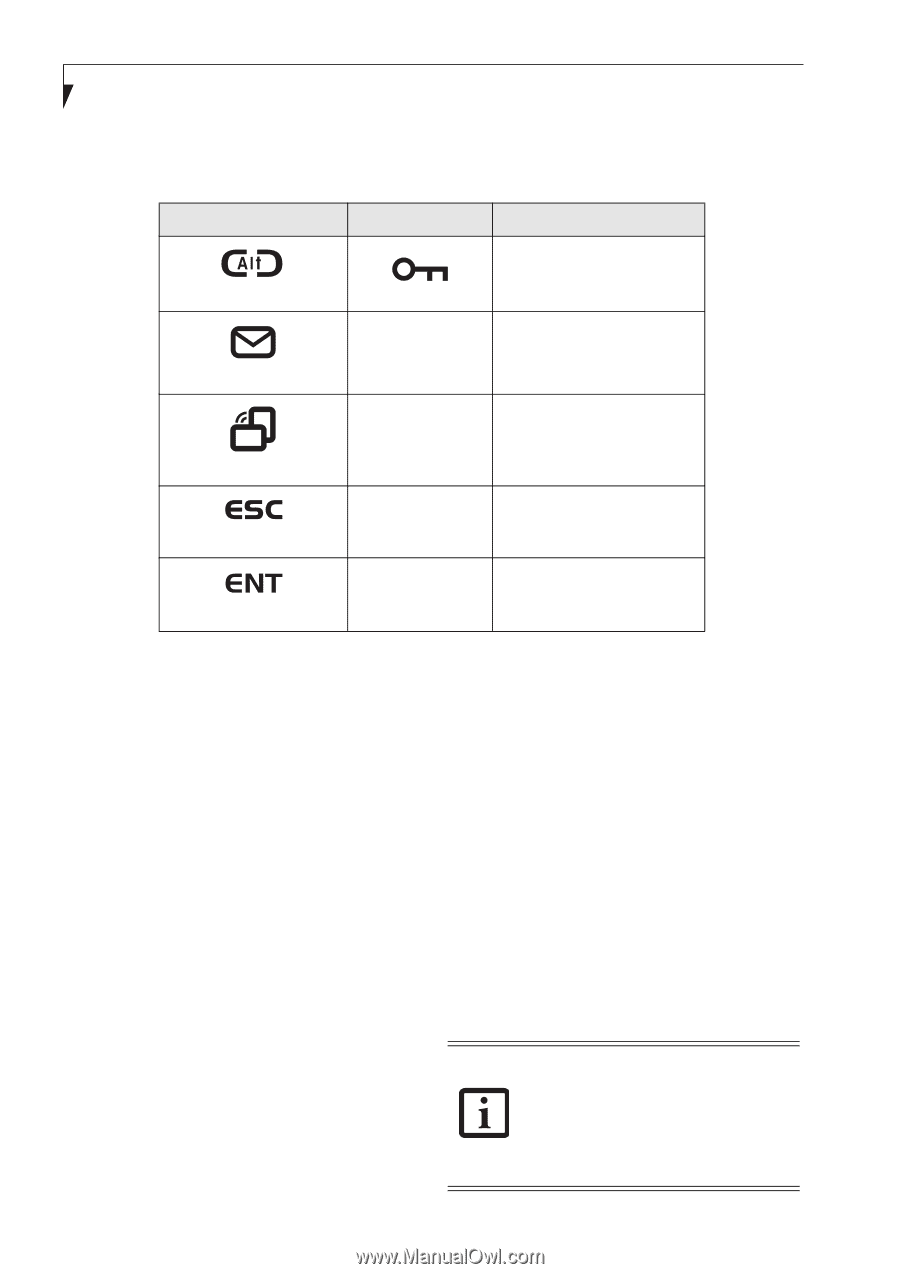
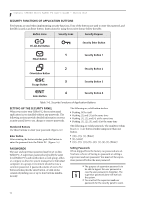
Stylistic ST5000 Series Tablet PC User's Guide - Section One SECURITY FUNCTIONS OF APPLICATION BUTTONS Five buttons are used when implementing security functions. Four of the buttons are used to enter the password, and the fifth is used as an Enter button. Instructions for using the security feature follow the table. Button Icons Security Icons Security Purpose Ctl-Alt-Del Button Security Enter Button 1 Security Button 1 EMail Button 2 Orientation Button Security Button 2 3 Security Button 3 Escape Button Enter Button 4 Security Button 4 Table 1-6. Security Functions of Application Buttons SETTING UP THE SECURITY PANEL When you receive your Tablet PC, the security panel application is pre-installed without any passwords. The following sections provide detailed information on your security panel, how to set, change or remove passwords. Numbered Buttons Use these buttons to enter your password.(Figure 1-6) Enter Button After entering the button strokes, push this button to enter the password into the Tablet PC. (Figure 1-6) The following are valid button strokes: ■ Pushing [4] by itself ■ Pushing [2] and [3] at the same time ■ Pushing [1], [2], and [4] at the same time ■ Pushing [1], [2], [3], and [4] at the same time The following are valid passwords. The numbers within braces ({ }) are button strokes using more than one button. ■ {[2]+[3]}, [1], [Enter] ■ [4], [enter] ■ {[1]+[3]}, {[2]+[3]+[4]}, [1], [4], [2], [Enter] PASSWORDS The user and supervisor password may be set on this Tablet PC. A supervisor password is typically the same for all Tablet PC's and notebooks in a work group, office, or company to allow for system management. Individual computers in a group environment should not use a common password. A password consists of one to five button strokes plus the enter button. A valid stroke consists of pushing one or up to four buttons simultaneously. Setting Passwords When shipped from the factory, no passwords are set. You have a choice of having no password or setting a supervisor and user password. You must set the supervisor password before the user password. ■ The purpose of supervisor password is to be able to bypass the user password in case the user password is forgotten. The supervisor password alone will not lock the system. ■ You must set the supervisor and user passwords for the security panel to work. 14