HP BladeSystem bc2000 Cisco Network Access Control for HP Thin Clients and CCI - Page 5
Configuring Policy Settings, Testing Methods, Thin Client Policy, Clean Access, Device Management
 |
View all HP BladeSystem bc2000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 5 highlights
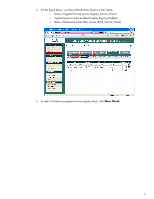
SYST RPS STAT DUPLX SPEED POE MODE 1 2 1X 3 4 5 6 2X 7 8 9 10 11 12 13 14 15 16 17 18 15X 17X 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 31X 33X 35 36 37 38 39 40 41 42 43 44 45 46 47 48 47X 16X 18X 32X 34X 48X Catalyst 3560 SERIES PoE-48 1 3 2 4 CISCO 3560 Switch CAM Appliance CAM console to switch port 3 Trusted interface to switch port 1(trunk) CAS Appliance Untrusted interface to switch port 4 VPN information VPN Group Name - cisco VPN Group Password - cisco VPN Username - jeremy VPN Password - cisco123 HP clients to switch ports 5 & 6 HP Compaq t5720 Thin Clients IP Addresses HP CCI Blade System VPN Private - 10.2.2.1 VPN Public - 10.1.1.1 Switch VLAN 2 - 10.2.2.2 Switch VLAN 3 - 10.3.3.2 Switch VLAN 4 - 10.4.4.2 Switch VLAN 5 - 10.5.5.2 Switch VLAN 6 - 10.6.6.2 CAM - 10.3.3.3 CAS Untrusted - 10.4.4.4 CAS trusted - 10.4.4.4 Client VPN - 10.1.1.2 Thin Client - 10.5.5.5 Figure 1 - Reference network topology The Cisco 3560 switch is configured with VLANs assigned to ports 1 to 5, as shown in Figure 1 above. Full switch configuration settings can be found in Appendix A - CISCO 3560 Switch Configuration. Configuring Policy Settings As we are focusing on the integration of NAC into a CCI and thin client network, we are exploring only the network policy enforcement settings that are pertinent to thin clients and blade PCs. This does not exhaust all the features of the Cisco NAC solution. Likewise, in a production environment, you may wish to validate many more OS configuration components than are discussed in this reference white paper. Testing Methods Tests for compliance are configured in stages via the CAM console for CAS to enforce. First we define checks, each of a single Windows registry setting, service status, program run state, etc. We then define rules as a combination of checks using AND/OR logical operators. We then construct requirements assigned to user roles and encompassing any or all rules we've defined. Thin Client Policy 1. Use the Web browser to connect to the Clean Access Manager console at https://10.3.3.3. 2. Click Clean Access under Device Management in the left panel. 3. Click the Clean Access Agent tab, and then click Rules. 5