HP BladeSystem bc2200 Embedded Web System User Guide for the HP BladeSystem PC - Page 27
Configuring Device Security
 |
View all HP BladeSystem bc2200 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 27 highlights
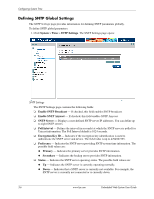
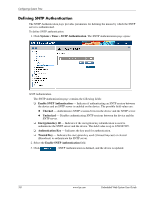
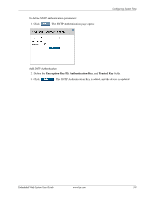
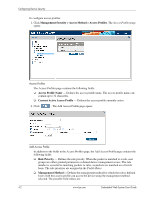
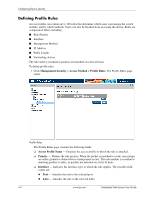
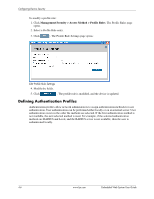
4 Configuring Device Security This section provides access to security pages that contain fields for setting security parameters for ports, device management methods, users, and server security. This section contains the following topics: ■ Configuring Authentication Methods ■ Configuring Network Security Configuring Authentication Methods This section provides information for configuring device authentication methods. This section includes the topics: ■ Defining Access Profiles ■ Defining Profile Rules ■ Defining Authentication Profiles ■ Mapping Authentication Methods ■ Defining RADIUS Settings ■ Defining TACACS+ Authentication ■ Configuring Passwords Defining Access Profiles Access profiles are profiles and rules for accessing the device. Access to management functions can be limited to user groups. User groups are defined for interfaces according to IP addresses or IP subnets. Access profiles contain management methods for accessing and managing the device. The device management methods include: ■ All ■ Telnet ■ Secure Telnet (SSH) ■ HTTP ■ SNMP ■ HTTPS Management access to different management methods may differ between user groups. For example, User Group 1 can access the switch module only via an HTTPS session, while User Group 2 can access the switch module using both HTTPS and Telnet sessions. The Access Profiles page contains the currently configured access profiles and their activity status. Assigning an access profile to an interface denies access using other interfaces. If an access profile is assigned to any interface, the device can be accessed by all interfaces. Embedded Web System User Guide www.hp.com 4-1