HP CM8000 Practical IPsec Deployment for Printing and Imaging Devices - Page 130
Kerberos, Active Directory, and Jetdirect
 |
View all HP CM8000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 130 highlights
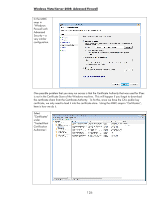
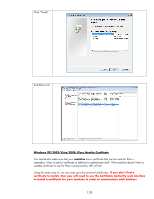
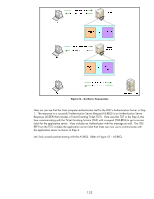
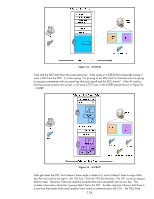
Here is the computer's IPsec certificate. Certificate authentication is one of the recommended authentication methods for production environments. It is very useful for those environments that already have a PKI in place and we can leverage that PKI for IPsec. What if the environment doesn't have a PKI in place? Are there any alternatives to use for authentication in a production environment? Yes - we have one more authentication scheme to cover (hang in there!). It is called Kerberos. Kerberos, Active Directory, and Jetdirect With Microsoft's Active Directory (AD), users and computer objects are created in AD and logically represent physical users and physical computers. Most administrators recognize that a user logs into the directory, but with AD, computers also login. Both login processes use the same protocol and that protocol is called Kerberos. Kerberos uses symmetric cryptography and as a result, has to figure out a way to securely distribute keys. To accomplish this, there is a shared secret key repository called the Key Distribution Center or KDC. Each computer has its own password that it knows and the KDC knows as well. The KDC is the trusted "third party", much like the certificate authority with the exception that the KDC knows the symmetric key of the user, while a certificate authority doesn't know the private key of the user. This means the computer system that hosts the KDC needs to be pretty secure since its compromise would reveal the secret keys of all users and computers under its control. Not a good thing. Kerberos was originally designed by MIT and was deployed in many security conscious UNIX environments. When Microsoft developed AD, they needed a well tested security protocol to provide Authentication for users and computers. They chose Kerberos. Users and computers that are members of the AD have everything in place to begin using Kerberos immediately. Users and computers that are not members of the AD have to jump through a few hoops to receive the benefits of Kerberos. Since HP Jetdirect is not a member of an AD domain as a computer object, it must jump through these hoops as well. Although it is not intuitive at first, we will create a user object to describe the HP Jetdirect. Jetdirect will act like a user and login and authenticate itself to the directory. Jetdirect's name is known in Kerberos terminology as the "Principal". The password for the Jetdirect user object is stored in the KDC as well as in the Jetdirect device. The domain in which the Jetdirect user object exists is called the "Realm", in Kerberos terminology. Jetdirect supports Intra-Realm authentication but does not support cross-Realm authentication. Essentially, any machines using Kerberos authentication must 130