HP CM8000 Practical IPsec Deployment for Printing and Imaging Devices - Page 46
IPsec Guidelines for Printing and Imaging Devices
 |
View all HP CM8000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 46 highlights
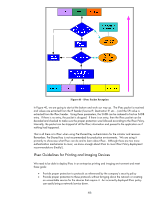
Figure 40 - IPsec Packet Reception In Figure 40, we are going to start at the bottom and work our way up. The IPsec packet is received and values are extracted from the IP header (Source IP, Destination IP, etc...) and the SPI value is extracted from the IPsec header. Using these parameters, the SADB can be indexed to find an SADB entry. If there is no entry, the packet is dropped. If there is an entry, then the IPsec packet can be decoded and checked to make sure the proper protection was followed according to the IPsec Policy. Internally, the packet can be stripped of all the IPsec information and passed to the application as if nothing had happened. That is all there is to IPsec when using Pre-Shared Key authentication for the initiator and receiver. Remember, Pre-Shared key is not recommended for production environments. We are using it primarily to showcase what IPsec can do and to learn about IPsec. Although there are two more authentication mechanisms to cover, we know enough about IPsec to cover IPsec Policy deployment recommendations (finally!). IPsec Guidelines for Printing and Imaging Devices We need to be able to deploy IPsec in an enterprise printing and imaging environment and meet these goals: • Provide proper protection to protocols as referenced by the company's security policy • Provide proper protection to these protocols without bringing down the network or creating an unavailable service for the devices that require it. An incorrectly deployed IPsec policy can easily bring a network/service down. 46