HP Integrity rx1600 Installation Guide, Second Edition - HP Integrity rx1600 - Page 23
Removing and Replacing the Cover, Removing the Cover
 |
View all HP Integrity rx1600 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 23 highlights
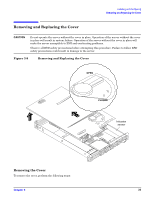
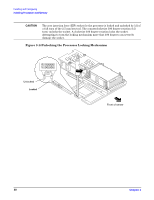
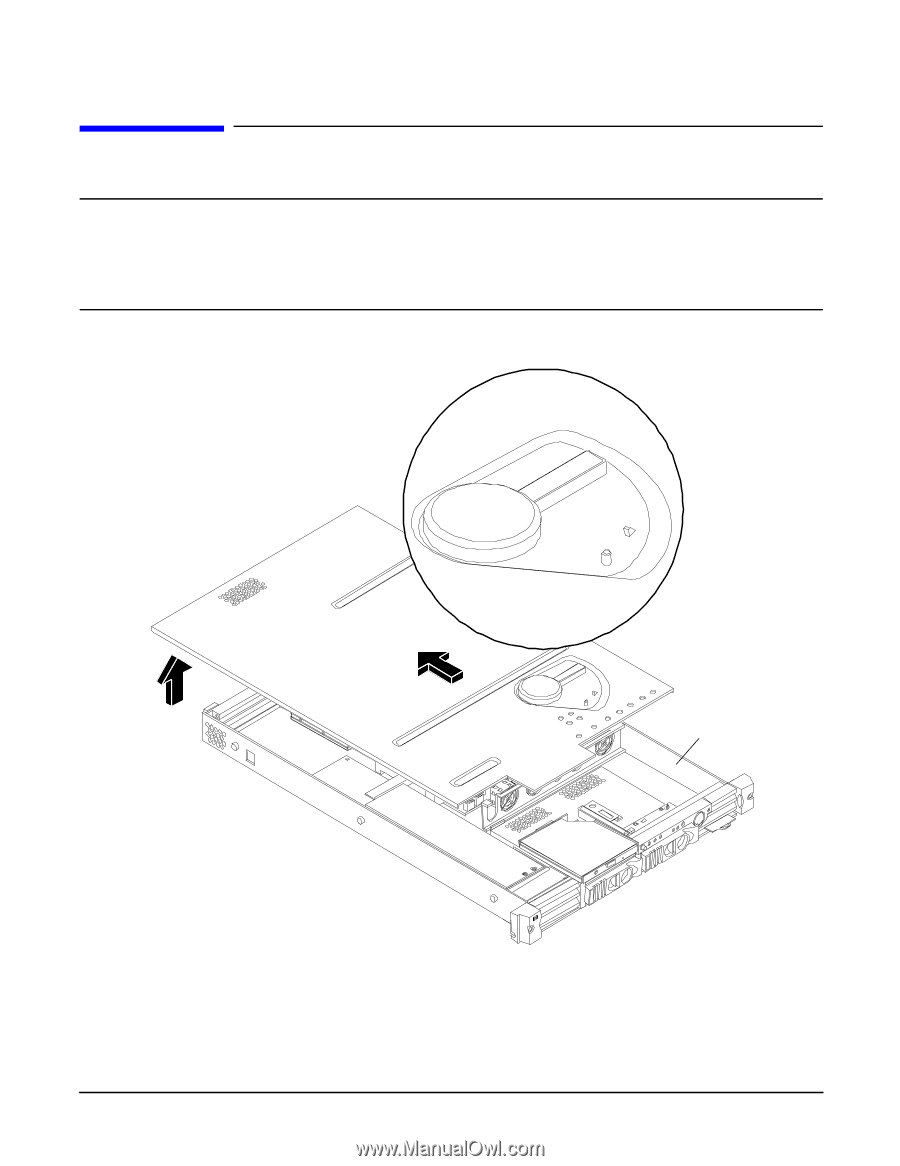
Installing and Configuring Removing and Replacing the Cover Removing and Replacing the Cover CAUTION Do not operate the server without the cover in place. Operation of the server without the cover in place will result in system failure. Operation of the server without the cover in place will make the server susceptible to EMI and overheating problems. Observe all ESD safety precautions before attempting this procedure. Failure to follow ESD safety precautions could result in damage to the server. Figure 3-9 Removing and Replacing the Cover OPEN CLOSED Intrusion sensor Removing the Cover To remove the cover, perform the following steps: Chapter 3 23
Chapter 3
Installing and Configuring
Removing and Replacing the Cover
23
Removing and Replacing the Cover
CAUTION
Do not operate the server without the cover in place. Operation of the server without the cover
in place will result in system failure. Operation of the server without the cover in place will
make the server susceptible to EMI and overheating problems.
Observe all ESD safety precautions before attempting this procedure. Failure to follow ESD
safety precautions could result in damage to the server.
Figure 3-9
Removing and Replacing the Cover
Removing the Cover
To remove the cover, perform the following steps:
OPEN
CLOSED
Intrusion
sensor