Ricoh Aficio MP C3501 Security Target - Page 38
Organisational Security Policies, Assumptions - reviews
 |
View all Ricoh Aficio MP C3501 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 38 highlights
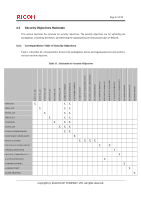
3.2 Organisational Security Policies The following organisational security policies are taken: Page 37 of 93 P.USER.AUTHORIZATION User identification and authentication Only users with operation permission of the TOE shall be authorised to use the TOE. P.SOFTWARE.VERIFICATION Software verification Procedures shall exist to self-verify executable code in the TSF. P.AUDIT.LOGGING Management of audit log records The TOE shall create and maintain a log of TOE use and security-relevant events. The audit log shall be protected from unauthorised disclosure or alteration, and shall be reviewed by authorised persons. P.INTERFACE.MANAGEMENT Management of external interfaces To prevent unauthorised use of the external interfaces of the TOE, operation of those interfaces shall be controlled by the TOE and its IT environment. P.STORAGE.ENCRYPTION Encryption of storage devices The data stored on the HDD inside the TOE shall be encrypted. P.RCGATE.COMM.PROTECT Protection of communication with RC Gate As for communication with RC Gate, the TOE shall protect the communication data between itself and RC Gate. 3.3 Assumptions The assumptions related to this TOE usage environment are identified and described. A.ACCESS.MANAGED Access management According to the guidance document, the TOE is placed in a restricted or monitored area that provides protection from physical access by unauthorised persons. A.USER.TRAINING User training The responsible manager of MFP trains users according to the guidance document and users are aware of the security policies and procedures of their organisation and are competent to follow those policies and procedures. Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.