TRENDnet TEW-639GR User Guide - Page 29
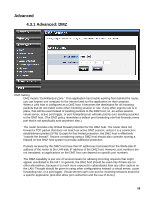
DMZ IP Address - forward port
 |
UPC - 710931600520
View all TRENDnet TEW-639GR manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 29 highlights
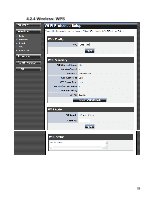
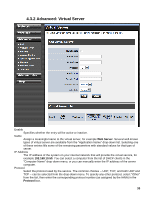
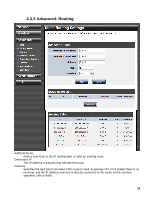
Port forwarding is rather like a selective DMZ, where incoming traffic targeted at one or more ports is forwarded to a specific LAN host (thereby not exposing as many ports as a DMZ host). Port triggering is a special form of port forwarding, which is activated by outgoing traffic, and for which ports are only forwarded while the trigger is active. Few applications truly require the use of the DMZ host. Following are examples of when a DMZ host might be required: ‧ A host needs to support several applications that might use overlapping ingress ports such that two port forwarding rules cannot be used because they would potentially be in conflict. ‧ To handle incoming connections that use a protocol other than ICMP, TCP, UDP, and IGMP (also GRE and ESP, when these protocols are enabled by the PPTP and IPSec Enable DMZ Putting a computer in the DMZ may expose that computer to a variety of security risks. Use of this option is only recommended as a last resort. DMZ IP Address Specify the LAN IP address of the LAN computer that you want to have unrestricted Internet communication. 29