ZyXEL B-220 User Guide - Page 25
Wireless LAN Security, Data Encryption with WEP, Fragmentation Threshold, RTS/CTS Threshold - wireless adapter
 |
View all ZyXEL B-220 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 25 highlights
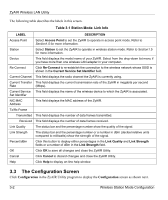
ZyAIR Wireless LAN Utility 2.2 Wireless LAN Security Wireless LAN security is vital to your network to protect wireless communications. Configure the wireless LAN security using the Security screen. If you do not enable any wireless security on your ZyAIR, the ZyAIR's wireless communications are accessible to any wireless networking device that is in the coverage area. 2.2.1 Data Encryption with WEP WEP (Wired Equivalent Privacy) encryption scrambles all data packets transmitted between the ZyAIR and the AP or other wireless stations to keep network communications private. Both the wireless clients and the access points must use the same WEP key for data encryption and decryption. There are two ways to create WEP keys in your ZyAIR. • Automatic WEP key generation based on a "password phrase" called a passphrase. The passphrase is case sensitive. You must use the same passphrase for all WLAN adapters with this feature in the same WLAN. For WLAN adapters without the passphrase feature, you can still take advantage of this feature by writing down the four automatically generated WEP keys from the Security screen of the ZyAIR Utility and entering them manually as the WEP keys in the other WLAN adapter(s). • Enter the WEP keys manually. Your ZyAIR allows you to configure up to four 64-bit or 128-bit WEP keys but only one key can be enabled at any one time. 2.3 Fragmentation Threshold A Fragmentation Threshold is the maximum data fragment size (between 256 and 2432 bytes) that can be sent in the wireless network before the ZyAIR will fragment the packet into smaller data frames. A large Fragmentation Threshold is recommended for networks not prone to interference while you should set a smaller threshold for busy networks or networks that are prone to interference. If the Fragmentation Threshold value is smaller than the RTS/CTS Threshold value (see previously) you set then the RTS (Request To Send)/CTS (Clear to Send) handshake will never occur as data frames will be fragmented before they reach RTS/CTS Threshold size. 2.4 RTS/CTS Threshold A hidden node occurs when two stations are within range of the same access point, but are not within range of each other. The following figure illustrates a hidden node. Both stations are within range of the access point (AP) or wireless gateway, but out-of-range of each other, so they cannot "hear" each other, that is they do not know if the channel is currently being used. Therefore, they are considered hidden from each other. Wireless LAN 2-5