Compaq ProLiant 1000 Performance Analysis and Tuning of Raptor's Eagle NT 3.06 - Page 5
such as Web Servers, News Servers, DNS Servers, FTP Servers, etc.
 |
View all Compaq ProLiant 1000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 5 highlights
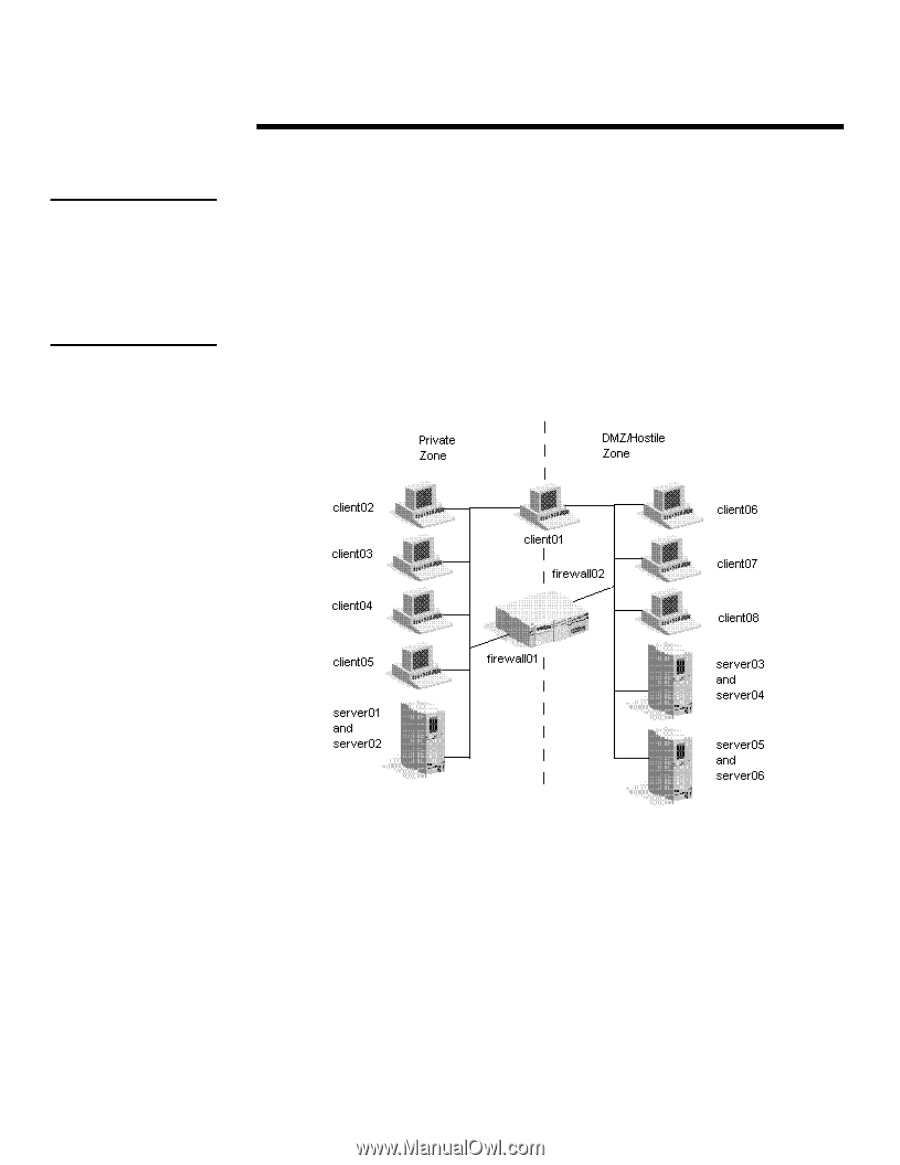
WHITE PAPER (cont.) Transaction refers to the amount of time it takes to open a connection from the client to the server, request data from the server, download that data from the server to the client, and closing the connection from the client to the server. Transactions are measured in Transactions Per Minute. (TPM) 278A/0497 ... This scenario, described in more detail below, is the scenario used in the benchmark tests for this paper. Performance ratings for the test runs are calculated from individual performance scores for the number of virtual clients used in the tests. Performance ratings are then translated into transactions per minute. This rating reflects the speed at which the firewall system processes network traffic, as it performs security tasks based on the security rule set. The security model that the NSTL Methodology uses specifies security zones, security rules, the protocols used in each security rule set, and logging. The benchmark creates load through the firewall by establishing multiple virtual clients on each physical client machine in each security zone. A control client is used to send requests to each physical client that dictates the number of virtual clients it used and gathers, from the virtual clients, the transaction information used to calculate the transactions per minute. (See Figure 1) Inside Outside Figure 1: Test Bed Configuration Three areas determine security zones: • Private Zone - the secure area of the network or the area protected from the Internet with a firewall. Internal networks reside in the private area. • DMZ - the network area unsecured by the firewall. Usually Internet servers are located here such as Web Servers, News Servers, DNS Servers, FTP Servers, etc. • Hostile Zone - or public area, is the cloud of the Internet or the outside network. NSTL's benchmark can be run with the three zones implementing three network segments or with two network segments. When two network segments are used, the DMZ and the Hostile Zone are combined. This is the setup selected for performance evaluation of Raptor's Eagle NT 3.06 contained in this paper. 5