Compaq ProLiant 1000 Performance Analysis and Tuning of Raptor's Eagle NT 3.06 - Page 9
Authorization
 |
View all Compaq ProLiant 1000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 9 highlights
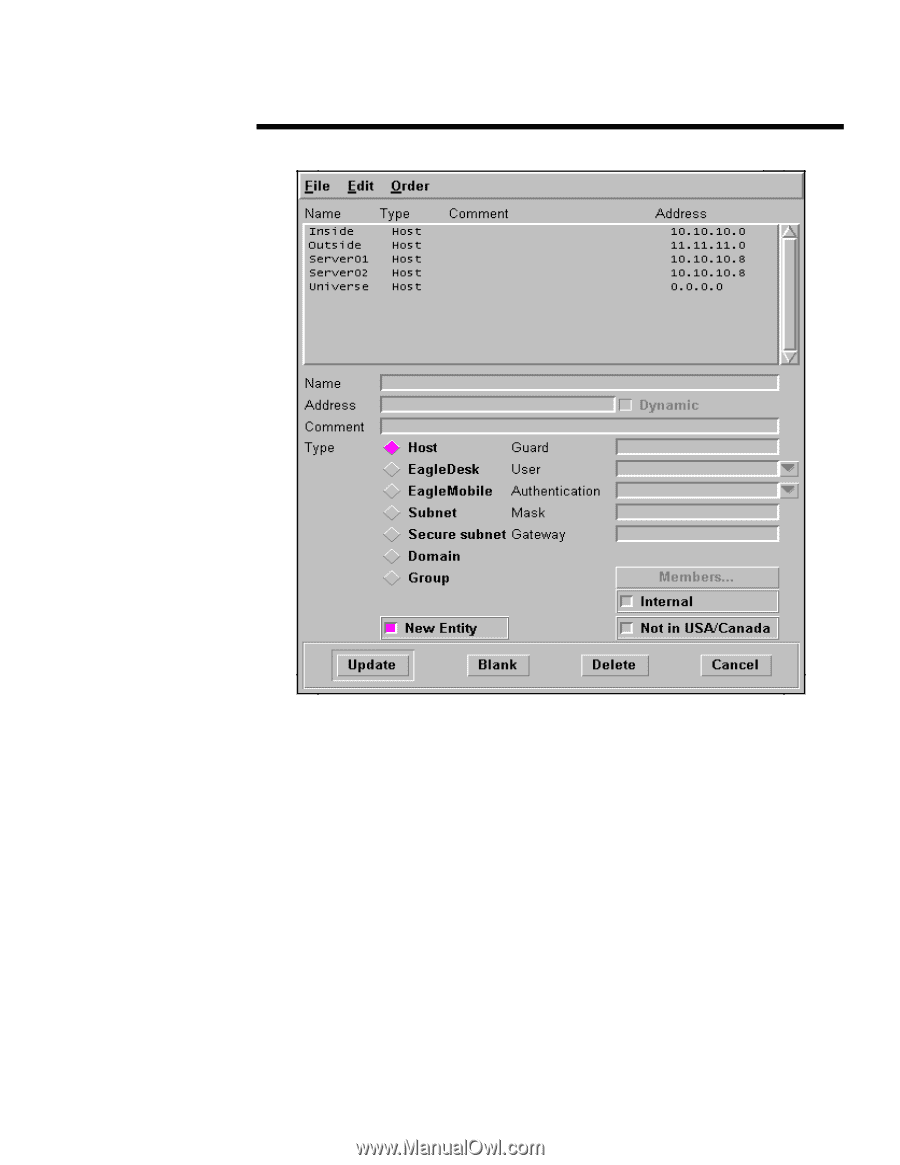
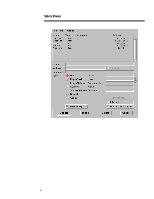
278A/0497 WHITE PAPER (cont.) ... Screen 2: Network Entries Eagle NT promotes transparency of IP addresses, meaning the only IP address the DMZ/Hostile zone can see is the outside interface of the firewall. Specifically, FTP transfers from the outside to the inside must first be connected to the firewalls outside interface, the FTP username becomes Error! Reference source not found., and the password becomes the password for FTP at the FTP server. More authentication may be required by the firewall depending on the rule set. HTTP transfers from the outside to the inside must be directed to the firewalls outside interface. If an inside HTTP server has been configured as in Screen 2, the firewall checks the rule base to ensure that traffic is allowed to pass, then makes a connect request to the Web server. The client on the outside sees only the destination and source IP addresses of the outside interface of the firewall in the IP packet header. This technique is similar to address translation, except in an application firewall such as the Eagle NT 3.06, you get this feature for free. Finally, the rules are configured to allow access from Private clients to Private servers, Private clients to DMZ/Hostile Servers, and DMZ/Hostile clients to specified Private servers. The convention of Inside and Outside mapping to Private and DMZ/Hostile was used. Also, note that specific rules must exist for access from the DMZ/Hostile network to the private network. Refer to the Screen 3, the Authorization screen. FTP setup is also done at the Authorization screen. All rules have the FTP GET check box selected. 9