Compaq ProLiant 1000 Performance Analysis and Tuning of Raptor's Eagle NT 3.06 - Page 7
Eagle NT 3.06 Firewall Setup of Base System - proliant 2000
 |
View all Compaq ProLiant 1000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 7 highlights
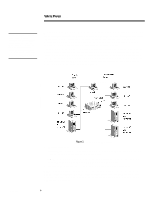
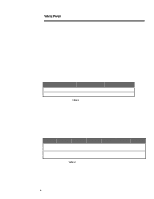
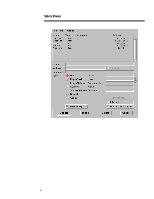
278A/0497 WHITE PAPER (cont.) ... Using NSTL's two-zone configuration (private zone behind the firewall and DMZ and hostile zone in front of the firewall), two physical servers are located in the DMZ/hostile zone and one physical server is located in the private zone. Physical client configurations place the control station between the two network segments (client01), four clients in the private zone (client02 through client05), and three clients in the DMZ/hostile zone (client06 through client08). Having the control station between both network segments allows data to flow across both networks with no interaction with the firewall, thus simulating real FTP and HTTP network traffic. Also, the control station is used to gather transaction time information and send virtual client load information to the physical clients on port (2001). Please refer to Figure 1 for a pictorial view of the testbed. Test Bed Setup Table 3 describes the hardware and software for the clients and web servers used in the test bed setup. All clients and servers are connected to a 100Mb network except for one test set, which connects clients and servers to a 10Mb network. Network configurations are discussed in the section Hardware and Software Tuning Characteristics. Machine Hardware OS Software Client01 ProLiant 2000, 2Pentium/90, 64 MB RAM, 2 EISA NetFlx-3 10/100 NIC, ON BOARD SCSI, 2 GB Drive Windows NT 4.0 Workstation, Service Pack 2 NSTL Firewall Benchmark Software for client machines, NSTL controller software client02 - client08 ProLiant 2000, 2Pentium/90, 32 MB RAM, 1 EISA NetFlx-3 10/100 NIC, ON BOARD SCSI, 2 GB Drive Windows NT 4.0 Workstation, Service Pack 2 NSTL Firewall Benchmark Software for client machines server01 - server06 ProLiant 2000, 2Pentium/90, 32 MB RAM, 1 EISA NetFlx-3 10/100 NIC, ON BOARD SCSI, 2 GB Drive Windows NT 4.0 Server, Service Pack2 Microsoft IIS 3.0 configured with FTP and HTTP Table 3: Client and Server Hardware Makeup Eagle NT 3.06 Firewall Setup of Base System The hardware and software setup for Raptor's Eagle NT 3.06 firewall starts with a base system configuration. Modifications are made to hardware and software on the firewall to determine performance differences from the base system. Determinations can be made at this point about how the firewall handles different configurations. An explanation about differences in the configurations and the reasons why such configurations were chosen are discussed in the section Hardware and Software Tuning Characteristics. This section discusses the hardware and software requirements for a base system configuration. It also shows the configuration of the Raptor Eagle NT 3.06 firewall using the GUI to the firewall (Hawk) and concentrates on the configuration items that do not change for all test runs. 7