Dell PowerConnect W-IAP175P Dell Instant 6.1.3.1-3.0.0.0 User Guide - Page 110
Walled Garden Access, Creating a Walled Garden Access
 |
View all Dell PowerConnect W-IAP175P manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 110 highlights
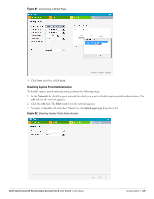
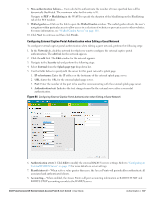
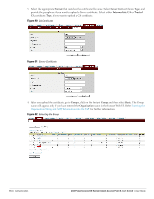
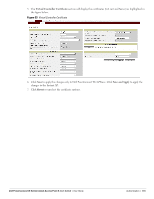
Figure 85 Configuring MAC Authentication 5. Click Next and then click Finish to apply the changes. Walled Garden Access On the Internet, a walled garden typically controls a user's access to web content and services. The walled garden directs the user's navigation within particular areas to allow access to a selection of websites or prevent access to other websites. Creating a Walled Garden Access Walled garden access is needed when an external captive portal is used. A common example could be a hotel environment where unauthenticated users are allowed to navigate to a designated login page (for example, a hotel website) and all its contents. Users who do not sign up for Internet service can view "allowed" websites (typically hotel property websites). The website names must be DNS-based (not IP address based) and support the option to define wildcards. This works for client devices with or without HTTP proxy settings. When a user attempts to navigate to other websites not configured in the white list walled garden profile, the user is redirected back to the login page. In addition, the black listed walled garden profile is configured to explicitly block navigation to websites from unauthenticated users. 110 | Authentication Dell PowerConnect W-Series Instant Access Point 6.1.3.1-3.0.0.0 | User Guide