Dell PowerConnect W-Series FIPS Dell PowerConnect W-6000M3 and W-3000 Controll - Page 11
Intended Level of Security, Physical Security
 |
View all Dell PowerConnect W-Series FIPS manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 11 highlights
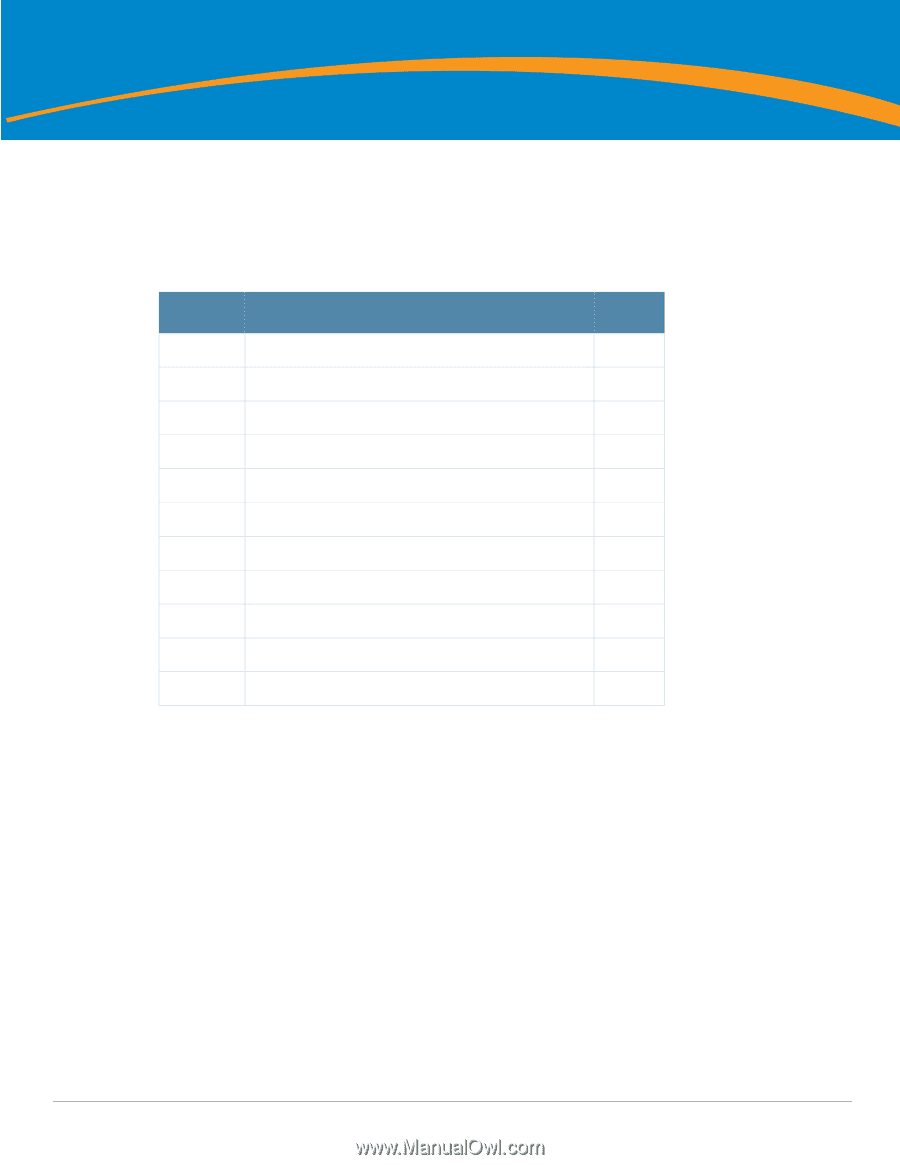
Chapter 2 FIPS 140-2 Level 2 Features Intended Level of Security The Aruba 3000 and 6000/M3 Controllers and associated modules are intended to meet overall FIPS 140-2 Level 2 requirements as shown in Table 2. Table 2 Intended Level of Security Section Section Title Level 1 Cryptographic Module Specification 2 2 Cryptographic Module Ports and Interfaces 2 3 Roles, Services, and Authentication 2 4 Finite State Model 2 5 Physical Security 2 6 Operational Environment N/A 7 Cryptographic Key Management 2 8 EMI/EMC 2 9 Self-tests 2 10 Design Assurance 2 11 Mitigation of Other Attacks 2 Physical Security The Aruba Controller is a scalable, multi-processor standalone network device and is enclosed in a robust steel housing. The switch enclosure is resistant to probing and is opaque within the visible spectrum. The enclosure of the switch has been designed to satisfy FIPS 140-2 Level 2 physical security requirements. For the Aruba 6000 the left, top, right, and bottom surfaces are irremovable. The rear panel can be removed by unscrewing fifteen screws. The switch has a number of hot-swappable components at front side, including four slots for supervisor and line cards, one fan tray, and three power supplies. Each of the components is attached with two screws. For the Aruba 3000-series the left, right, front, rear, and bottom surfaces are irremovable. The top panel can be removed by unscrewing two screws. A metallic opaque shield is installed at the factory during manufacturing and can not be removed by the User. For physical security, the Aruba 6000 switch requires Tamper-Evident Labels (TELs) to allow the detection of the opening of the chassis covers; the removal or replacement of any module or cover plate, and to block the Serial console port. Aruba 3000, 6000/M3 and Dell W-3000, W-6000M3 | FIPS 140-2 Level 2 Release Supplement FIPS 140-2 Level 2 Features | 11