Dell PowerConnect W-Series FIPS Dell PowerConnect W-6000M3 and W-3000 Controll - Page 27
Tamper-Evident Labels
 |
View all Dell PowerConnect W-Series FIPS manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 27 highlights
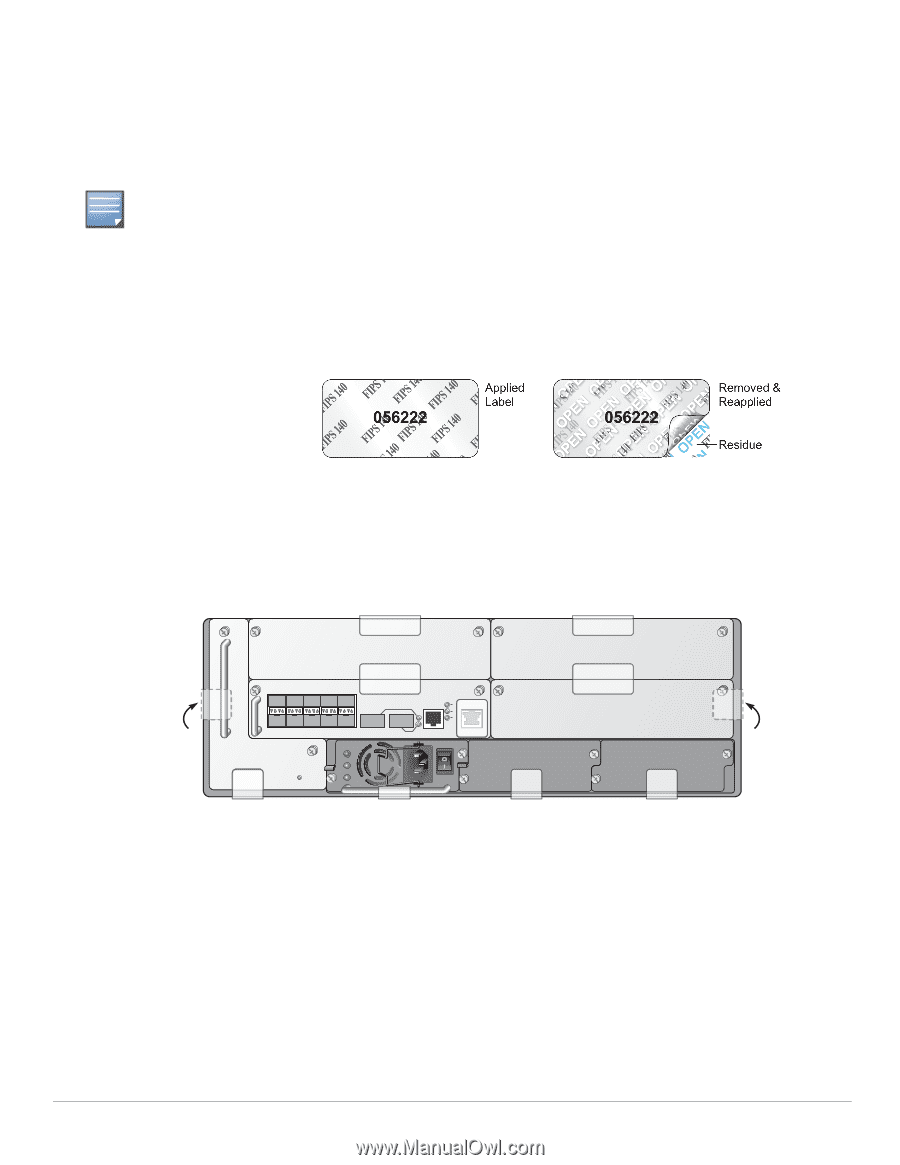
NOTE Tamper-Evident Labels After testing, the Crypto Officer must apply Tamper-Evident Labels (TELs) to the switch. When applied properly, the TELs allow the Crypto Officer to detect the opening of the chassis cover, the removal or replacement of modules or cover plates, or physical access to restricted ports. Vendor provides FIPS 140 designated TELs which have met the physical security testing requirements for tamper evident labels under the FIPS 140-2 Standard. TELs are not endorsed by the Cryptographic Module Validation Program (CMVP). The tamper-evident labels shall be installed for the module to operate in a FIPS Approved mode of operation. Reading TELs Once applied, the TELs included with the switch cannot be surreptitiously broken, removed, or reapplied without an obvious change in appearance: Figure 3 Tamper-Evident Labels Each TELs also has a unique serial number to prevent replacement with similar labels. Required TEL Locations The Aruba 6000 Controller requires a minimum of 11 TELs to be applied as follows: Figure 4 Required TELs for the Aruba 6000 Mobility Controller 3 4 1 7 5 6 11 9 10 8 To Detect Opening the Chassis Cover 1. Spanning the left side and rear of the chassis 2. Spanning the right side and rear of the chassis To Detect the Removal of Any Module or Cover Plate 3. Spanning the Slot 2 faceplate or blank and the top of the chassis 4. Spanning the Slot 3 faceplate or blank and the top of the chassis 5. Spanning the Slot 0 faceplate or blank and the Slot 2 faceplate or blank 6. Spanning the Slot 1 faceplate or blank and the Slot 3 faceplate or blank 2 arun_0118B Aruba 3000, 6000/M3 and Dell W-3000, W-6000M3 | FIPS 140-2 Level 2 Release Supplement Installing the Controller | 27