Dell PowerEdge M1000e Web Tools Administrator’s Guide - Page 259
Basic IPsec configurations, Encapsulating Security Payload, Endpoint to Endpoint, Gateway to Gateway
 |
View all Dell PowerEdge M1000e manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 259 highlights
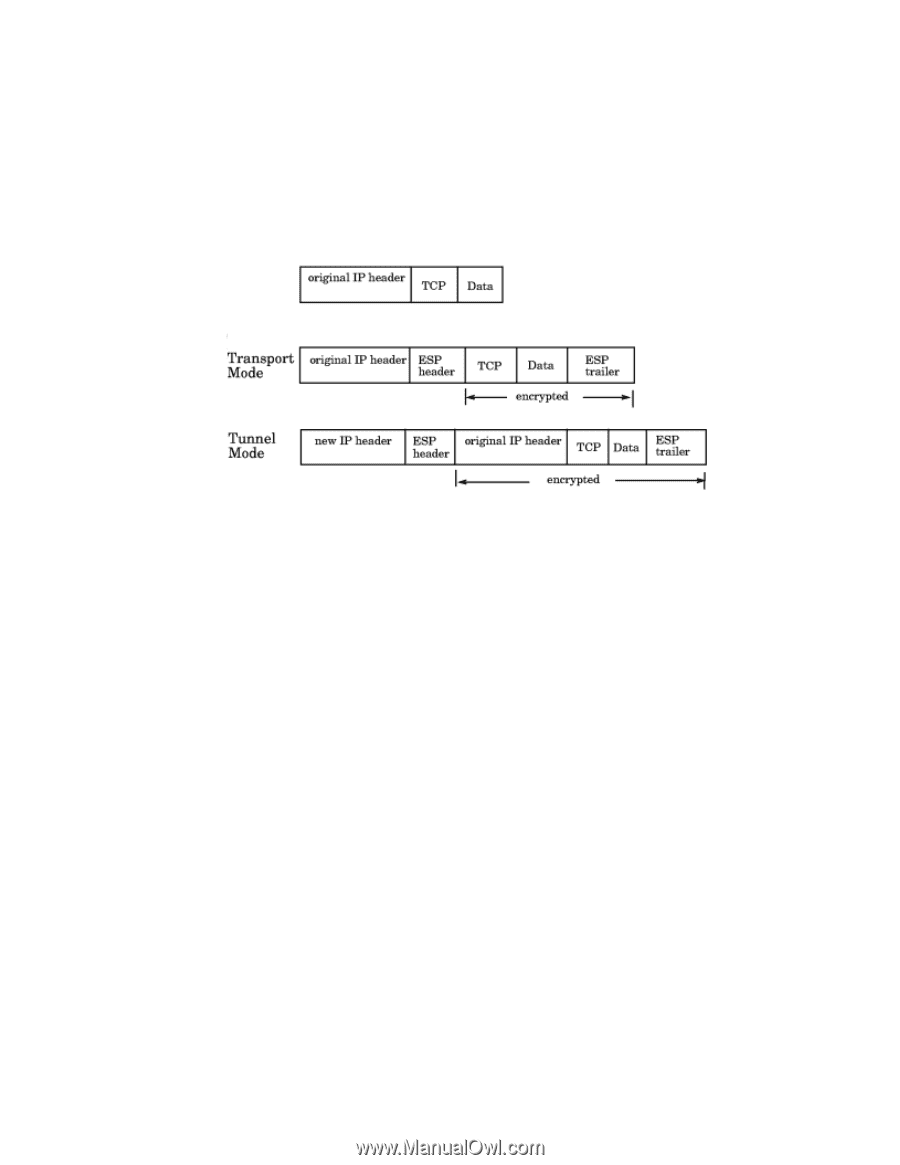
DRAFT: BROCADE CONFIDENTIAL IPsec concepts 17 Encapsulating Security Payload ESP provides authentication, and also provides privacy by encrypting the IP datagram. The use of an ESP header is similar to the use of the AH header. A hash algorithm is used to calculate an authentication value, the authentication value is sent in an IP datagram, and the same hash algorithm is used by the receiver to verify the authentication value. ESP can be used in either transport mode or tunnel mode, as shown in Figure 62. FIGURE 62 ESP header in transport mode and tunnel mode Basic IPsec configurations There are three basic configurations for IPsec use: • Endpoint to Endpoint • Gateway to Gateway • Endpoint to Gateway Endpoint to Endpoint In an endpoint to endpoint configuration, both endpoints implement IPsec. Transport mode is commonly used in endpoint to endpoint configurations, and only a single pair of addresses is used. Typically, this kind of configuration would be used for direct communication between hosts. There are two drawbacks to consider: • If network address translation (NAT) is used on the connection, one or both endpoints may be behind a NAT node. If that is the case, UDP must be used to encapsulate the tunneled packets. Port numbers in the UDP headers can then be used to identify the endpoint behind the NAT node. • Packets cannot be inspected or modified in transit. This means that QoS, traffic shaping, and firewall applications cannot access the packets, and does not work. Gateway to Gateway In a gateway to gateway configuration, IPsec protection is implemented between network nodes. Tunnel mode is commonly used in a gateway to gateway configuration. A tunnel endpoint represents a set of IP addresses associated with actual endpoints that use the tunnel. IPsec is transparent to the actual endpoints. Web Tools Administrator's Guide 231 53-1001772-01